Vulnerabilities, viruses, and malware are some of the dangers prevailing in the cyber world. The average person may not be aware of current cyber events, but security researchers are well educated in this evolving world. Today, we are going to discuss Cross-Site Scripting vulnerability that is currently causing most cyber attacks.
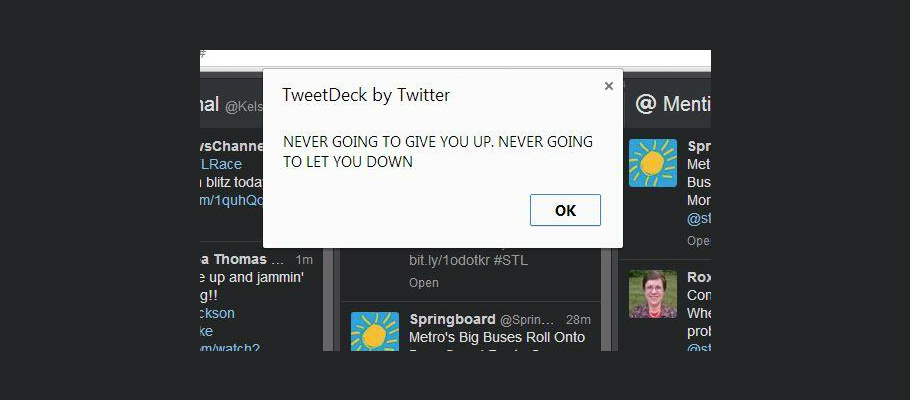
Recently, twitter dashboard service named as TweetDeck suffered from cross-site scripting attack. It allowed attackers to run a malicious code on user’s computer and tweeting behalf them. TweetDeck temporarily took down its service to assess the vulnerability. However, the authority has fixed the issue now. They urged users to log out completely of TweetDeck and log in back to apply the security fix.
What is Cross-Site Scripting?
Cross-Site Scripting or XSS attack is an injection attack in which malicious scripts are injected into trusted websites. An attacker sends out a malicious code to the end user’s web browser in the form of a browser side script targeting a web application. It occurs when a web application executes a script, which is not encoded, and attackers take advantage of a flaw in the application. Such unencrypted scripts are sent to the end user’s browser, and the browser cannot decide whether to trust the script or not. When a browser runs the script, a malicious code activates on the client side. A XSS attack steals cookies and session tokens of users and performs session hijacking.
Example of XSS Attack:
When you type any keyword in search box in any website it looks like below format.
<form action="search.php" method="get"> <input type="text" name="q" value=""/> <input type="submit" value="send"/> </form>
Here on search.php webpage, you will find keyword search in the form of “You Searched For”.
<h3>You Searched for: <!--?php echo($_GET['q']) ?-->
The search query will be displayed on the web page. If the web application has not encoded the input and has no filtration, then the attacker can inject malicious script which looks like below:
Search for
><script>alert(XSS injection)</script> <h3> You Searched for: ><script>alert(XSS injection)</script>
The browser will execute and it will show an alert box saying “XSS injection.”
Types of Cross-Site Scripting Attack:
Cross-Site Scripting can be classified into three categories: stored attacks, reflected attacks, and DOM based attack.
Stored XSS Attack:
Stored XSS attacks or persistent cross-site scripting attack happens when an XSS vector is already present in the website database. When a user opens a webpage, the code starts its operation. The Stored XSS attack is more effective than non-persistent XSS attacks because it automatically executes whenever a user opens the browser. In this type of attack, attackers do not need to interact with the web directly; they may use any system log or email to run malicious code on web applications.
Reflected XSS Attack:
Reflected or Non-Persistent attack is a common attack where the data provided by the client remains in HTTP or in HTML form, which is used by server-side scripts to show instant query results. These requests are not properly sanitized. This type of attack can be delivered via email or neutral website. It lures users and directs them to a trusted website, but it contains XSS vector. When a user clicks on such a link, the malicious code executes on the user’s browser.
DOM (Document Object Model) based Attack:
DOM based attack occurs when the DOM environment is modified by an attacker on a website, and users access it in the browser. However, the script starts to run in an unexpected way, and sometimes it baffles developers due to tricky working manner. The attacker’s payload does not contain on the server-side script, but it happens at the client-side script at runtime.
Impact of Cross-Site Scripting:
When attackers succeed in a XSS attack, they could take the following advantage on your PC system.
- Access to account credentials of the user on website
- Spread worms
- View user’s browser history
- Control the browser remotely
- Use of Intranet applications
- Link injection
- Data and content theft
How can you reduce a XSS Attack?
The golden rule of preventing XSS attack is to encode the data input and escape the data on output. To mitigate the risk of a XSS attack, you should focus on data validation, data sanitization, Cookie Security and output escaping. In all these techniques, the common factor is that you should authenticate data that you get from input.
Data Validation:
Data validation ensures that the application is running with the right data. Every piece of data must be authenticated to ensure that it is of the exact type. When the data fails to pass the validation process, it should be clear up. You can mitigate the risk of malicious script, by employing the data coding techniques, for example, URLEncode and HTMLEncode.
Data Sanitization:
Data Sanitization removes any unwanted bits from the data string and keeps the data in a normal format. It is sensible to remove HTML markup from the data string to keep data in plain text. Data sanitization is not an appropriate when you receive TEXT input from an HTML form; therefore, you should go for data encoding.
Cookie Security:
Many web applications have an additional security controls to handle cookie-based user authentication. These web applications establish authentication between individual HTTP requests on the base of session cookies. However, client-side scripts can access these cookies. Therefore, a XSS attack can steal these cookies. Many web applications connect session cookies with the logged in user’s IP address to reduce such situation, and allow that particular IP to use specified cookie.
Output Escaping:
HTML file holds both content and command. The command section for content includes headings, bold text, scripts, special characters, and images. You should escape the data when delivering it to the user to secure the integrity of the output data. Escaping ensures that characters are treated as data and the data is not meant to be accomplished. Untrusted data cannot be utilized to perform a XSS attack. This avoids the browser from enforcing any unplanned special series of characters.
Conclusion:
Cross-Site Scripting is one of the top five security attacks performed on a regular base by attackers. Many well-known sites including social media sites were held victim of this vulnerability. The Cross-Site Scripting or XSS attack targets web application, plug-ins, and the server. In this case, the above security precautions can help you to mitigate the risk of XSS attack.
Image Credit: Kelsey