Due to the evolution of internet and networking, online attacks became a major issue in the field of cyber security. Most of the financial activities are done through networking has kindled the hackers to make money by cyber attacks. Cyber hacking is done remotely and the user will not be able to sense the hacking activities. Even after the attack, the hackers are safe without being caught by their illegal activities. This article is a small revelation for the beginners to know about the mischief of the hackers. Here we discuss about the ways the hackers misuses the technology for making money and achieve their goals in a wrong path.
Botnets:
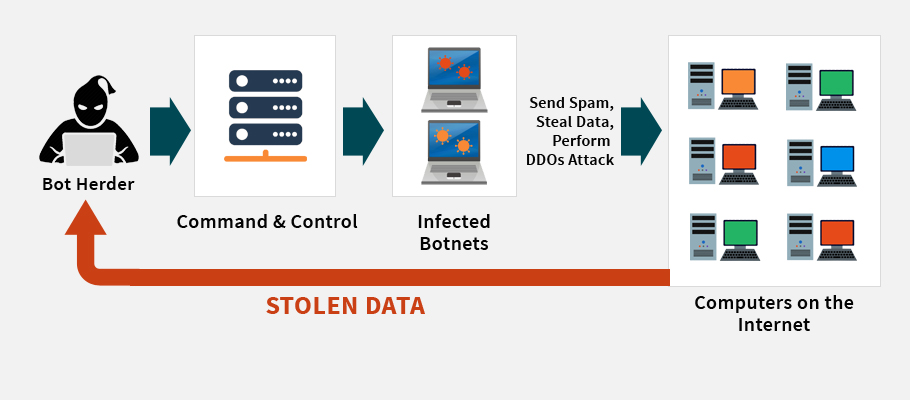
Bots refers to a small script, which is used to retrieve some specific data. The script enhances automated functions. This bots were now misused to isolate the connected computer devices online and getting the control of each devices in a remote place. This remote control of the isolated personal computer / electronic appliances will not be sensed by the owner of the devices. The hackers who were controlling the device will be able to inject malware to the hijacked personal computer and can control the activities of the device without the knowledge of the real owner of the device. They can silently watch the activities of the hijacked computers and achieve their goal. The controlled computer devices by the hackers are termed as Botnet devices.
DDoS Attack:
The acronym of DDoS is Distributed Denial of Service. This type of networking attack is done by denying the accessibility of the online resource for the user. This interrupts the normal connectivity with the network. DoS attack is applied for a single isolated computer whereas DDoS is accomplished with the help of Botnet devices. Initially the hackers use the bots to isolate the connected computers and then apply ‘DDos Attack‘ in order to interrupt their normal internet activities.
This type of attacks is classified as two categories. This classification is done based on the layer of the network get affected by the scripts injected by the hackers.
- Application Layer DDoS Attack
- Network Layer DDoS Attack
Application Layer DDoS Attack
This type of attack includes Http-Get flooding. This attack mainly concentrates in crashing the application. Initially it attacks the operating system, communication protocols etc. The first symptom of this attack in the system can be sensed by the low efficiency of the device. This attack gradually slows down the basic working of the device. The hackers mostly concentrate on government sites to increase the vulnerability of the attack.
Network Layer DDoS Attack
This attack concentrates the network layer of the connectivity of the devices. It includes UDP floods, SYN floods, NTP amplification, DNS amplification, ICMP flood attacks, SSDP amplification, IP fragmentation. DNS server get affected the most due to this attack. Here the bots are used to flood the DNS with multiple requests from botnet devices, which then result into network saturation.
Botnet Based DDoS Attack:
Researchers have classified this type of attack as three models. They are:
- Agent-Handler Model
- Internet Relay Chat (IRC) Model
- Web-based Model
Agent-Handler Model
In this model, three members in the network do the hacking. The hackers initially use the bots to get control of the devices, which have been connected, through internet. Agents are the compromised systems of the hackers use this handler software to get control of the victim. The attackers watch out the network continuously and install this handler software on the compromised router and network server. The compromised system owners will not be aware of their loss of control over the network. After accomplishing this, the hackers are now ready to play their mischief using the compromised devices and the controlled network.
Internet Relay Chat (IRC) Model
This attack is similar to the agent handler model but here instead of handler software, hackers use the IRC channel to communicate between the agent and the victim. This model enhances the attackers in concealing their control over the network with less difficulty.
Web-based Model
The hackers rarely use this method. Most of them prefer IRC model because of its concealing efficiency. This method was not suited for hacking large-scale organization data. The model is easy to set up and has improved command functions than any other method. Moreover, the attack can be performed with less bandwidth and easy to use.
The above-discussed models have been designed as tools by the hackers for automatic functionality over the network.
- Agent-based DDoS Attack Tools
- IRC-based DDoS Attack Tools
- Web-based DDoS Attack Tools
Botnet And DDoS Attack Victims
Large-scale organizations who rely on internet for their daily activities for the processing of their business were the great victims of these types of attacks. E-commerce and stock exchange based businesses were badly affected by these hackers and they spend thousands of million dollars to protect themselves from these hacking activities. This type of attacks is a major threat to the online community who rely on internet for the development of their career. Most of the hackers focus on big revenue generating organization, which has a million dollars business handling in their day-to-day activities. Financial losses bring down the economy of the country. This attack is a threat to the country and the government should take steps in reducing this type of attacks by using safe tools to resist those attacks.
Conclusion:
This is a serious problem in the current scenario as it affects the economy of the country and brings about a financial crisis within few minutes. Even though there are many protecting services all over the world but still this problem has not been overcome 100%. Still every now and then, the network was hacked without the knowledge of the owner resulting in a major fall in the economy of the organization. The hackers are now well aware of the technologies and able to find loopholes in achieving their goals over the network. We the public should be knowledgeable in order to overcome the future crisis.