Just as the name suggests, malware is malicious software, which can be injected into website by hackers and installed into your computer usually through online sources and even offline. Identifying the likely sources of such harmful software would help to protect the website.
What Should Know About Malware?
Keep in mind that once computer is infected with malware, it can also put website at risk, since you access website on the computer. Hence, protecting computer would also protect your website.
Malware can cause various harmful effects, including:
- Stealing website passwords – The intent of such malware would be to gain access to website and maybe even lock you out altogether.
- Uploading phishing scripts – Malware can hijack account and use it to send fake emails to capture the recipient’s bank or online payment login details.
- Distributed Denial of Service (DDOS) attacks – Here, thousands of PCs are infected with malware attack and bring down a website through heavy traffic.
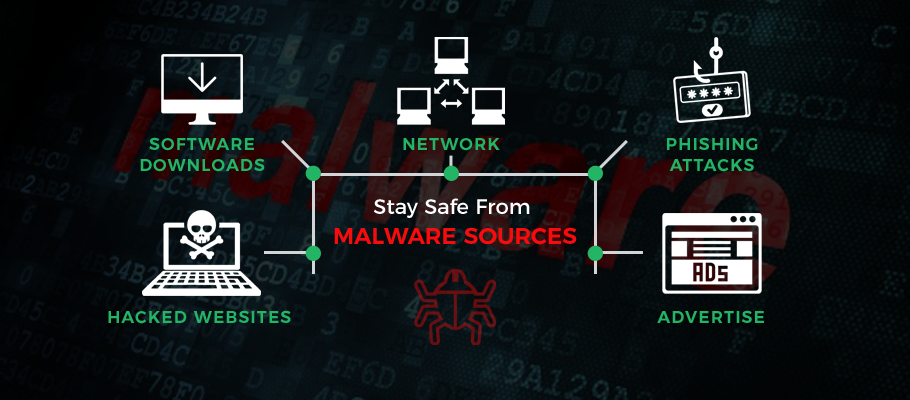
Sources of Malware
You can get malware as a Virus, Trojan, Adware and Worm, that each operates in its own way and infiltrates website or computer. Since malware can come from multiple sources, even those that you hardly expect, you should always be vigilant. Some of the sources include:
1. Networks
Any network can spread malware, whether intranet or internet and accessing network using wireless, LAN or other connectivity method. This can be achieved through a computer worm, which is a malware program that replicates itself with the purpose of spreading to other computers, thus, affecting your entire computer network. Usually, it spreads itself using a computer network that relies on security failures on the targeted computer to access it.
How to Deal With This:
- Connect to only secured networks, particularly wireless networks.
- Also, when browsing, only open websites that have SSL or TLS protocols, which authenticate and encrypt data.
- On the event that you catch a computer worm on one of your computers, it is advisable to check all the other computers in your network as well one by one, having disconnected all of them.
- A hacker may install a Remote Administration Tool (RAT) on your computer to use it to infect the other computers in your network.
2. Hacked Websites
Hackers could insert malicious code in a trusted website, if the owner isn’t aware of security holes in the sites’ setup. During accessing that trusted website, for example, the code may prompt you to download malware under the pretext of it being valuable software. You can easily fall for this since you already trust the website and wouldn’t suspect anything out-of-the-ordinary.
Hackers attack mostly to cause damage, steal information, and use the computer as a spam machine or for Denial of Service (DOS) attacks on other PCs. Their favorite targets are home, as well as home office computers connected to the internet, or broadband, since the internet connection remains open that creates an opportunity to locate scanners in the computers.
How to Deal With This:
- If you find anything that appears inappropriate in a website, seek confirmation from the website owner. This is particularly so with download options.
- To be on the safe side, only download software from sites that have a SSL certificate.
- Also, install firewalls on computer that prevent unauthorized access from the outside.
- The only people, who can access your computer besides yourself, should be those people to whom you have authorized.
3. Software Downloads
There are numerous types of useful software online available for users. Unfortunately, there are just as many, and may be even more software that contain malicious code. Just as the name suggests, malware happens to affect computer during software downloads through the internet. They usually require an installation process into computer to take place. You may be thinking it is harmless when downloading, but if the software download has malware, it may cause your computer more harm than good.
How to Deal With This:
- When downloading any form of software, from programs to games to updates to demos, through the internet, ensure the software is from a reliable source. Don’t take the bait, even if a website offers to download a well-known software or plugin like Flash for you.
- To be on the safe side, only download software from legitimate website/play store or software that have a valid Code Signing SSL certificate.
- Also, ensure that you run all software downloads through an antivirus upon completion.
- And the simplest way to avoid malicious software downloads is to read all the prompts during installation process to view what the program is all about.
4. Ads
You can end up downloading malicious code just by clicking on adverts in websites, including trusted websites. Such ads are designed to create urgency, such that you end up clicking without thinking about the consequences. For instance, some adverts claim they have detected a virus in the computer. Others offer to scan the computer to identify viruses that you haven’t noticed. Clicking those adverts could install malware in the computer.
How to Deal With This:
- Always consider the kind of adverts you click on and the websites where you find such ads. Ads in a trusted, secure website are much less likely to contain malware.
- Also, ensure that your browser plugins, web browsers, and all other operating systems are flawless and up-to-date.
- Anti-virus programs are also great at preventing malware ads from entering your computer as they recognize suspicious malware that may want to exploit your computer and stops them from installing. Hence, ensure your computer is installed with an updated one.
5. Phishing Attacks
Phishing, an attempt for unauthorized access to sensitive information like credit card, password and username details, is a very common source of malware. They come in the form of a disguise as a trustworthy entity asking you to provide your sensitive information and usually do not give you a lot of time to think, instead, they demand immediate action.
Some examples of such phishing attacks include offers of free iPads on Facebook, emails containing links or attachments, generic links or videos posted directly on social platforms, or video links with catchy titles like “Is this you in this video?” Clicking on such links or videos could expose to malware.
How to Deal With This:
- Read email properly and check email ID (whether it came from legitimate company/person) before clicking on link or download any attachment and fight against email phishing.
- If use any social media platform then be careful especially about Facebook apps you install and the extent of information they can access from your account. Preferably, don’t allow any apps to post on Facebook on your behalf.
- Additionally, the use of common sense would save you a whole lot of trouble. Phishing scams rely on quick actions, thus, take a few minutes to think things through and you shall find that you will see through the scams. Remember, when the offer is too good, think twice.
How To Protect Website/PC:
- Use Secure Sockets Layer (SSL) that encrypts information transferred between server and browser, making it impossible for unwanted parties to intrude.
- Always have strong Anti-Virus software installed and regularly updated in your computer.
- Run malware scan with GeoTrust Website Anti-Malware that identifies malicious code and activities and inform about malware to website/ owner.
- Always have regular automatic backup to protect website data to revert to incase of a malware attack.
- Always update your computer’s operating system, your website CMS (WordPress, Magento, Joomla…) and plugins, browser, and other computer programs whenever updates are available. Updates usually contain better security features.
- Use Web Application Firewalls, which keep attackers from accessing your website through legitimate traffic, including clients and search engine crawlers, while blocking spam bots, hackers and other malicious traffic.
- Use a custom CMS instead of a public CMS platform.
- If you are accepting payment via credit card then you should comply standards specified in PCI DSS as these compliances ensures business owners and customers that their payment is secured against cyber-attack and fraud. Failure to comply with these standards turn into financial loss, lawsuits, and government fines.
Conclusion
Beyond this knowledge, you should always keep abreast with new developments to safeguard your website and computer against new strains of malware.