Read here What is a Man-in-the-middle (MiTM) attack With the guide of how to prevent man-in-the-middle attacks?
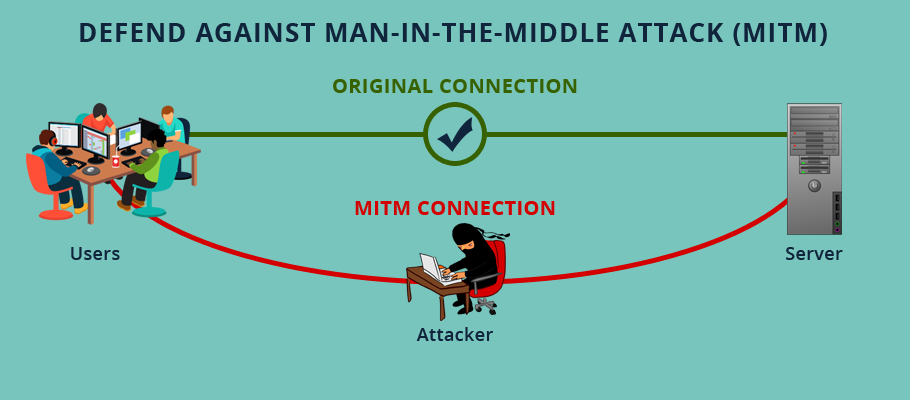
A Man In The Middle Attack (MITM) is a form of eavesdropping and is a cyber security issue where the hacker secretly intercepts and tampers information when data is exchanged between two parties.
It is almost similar to eavesdropping where the sender and the receiver of the message are unaware that there is a third person, a ‘Man in the Middle’ who is listening to their private conversations secretly.
How Are MITM Attacks Perpetuated?
In MITM (man-in-the-middle) attack, the attacker enters into a conversation between sender and receiver, gain access to the information and impersonate both endpoints that they are sending details to each other. However, the attacker intercepts ongoing communication without knowing to both endpoints. It is a type of eavesdropping and exposes real-time conversations or data transfer. Attacker can send, intercept, and receive data without awareness of the sender and receiver. It is a kind of session hijacking and other forms are Sidejacking, Evil Twin, sniffing, etc.
There are two types of MITM attack like attacker try to find unsecured WI-FI and insert tool between sender and receiver. In another method, the attacker injects malware into the computer, and then malware automatically install itself into the browser to the target and the other is the involvement of malware called man-in-the-browser (MITB) attack.
The Workflow Of MITM Attacks
Technically, Man In The Middle attacks take place in two phases:
- Interception
- Decryption
Interception
In the first phase, the user traffic is redirected through the hacker’s network before it reaches the sender or receiver’s system. Thus, the attacker is able to have an open view of the type of data and its contents that is being exchanged without any restriction. Secondly, neither the sender or receiver is aware that their traffic is being rerouted through an attacker’s network.
How Is The User Traffic Intercepted?
One common way of intercepting user traffic is to trap the user into using free public Wi-Fi hotspots which the user might use without any password protection. However, this usually fails since most users are wise enough to secure their systems with minimal password security.
In such cases, hackers adopt an even more adept way of intercepting the information. They may use one or more of the below mentioned tactics to achieve that:
-
IP Spoofing
The attacker masks himself as an application and changes headers of IP address. So, users attempting to access URL of an application will be redirected to attacker’s website.
-
ARP Spoofing
In ARP spoofing, the attacker sends fake ARP (Address Resolution Protocol) messages to the user’s system through the IP of another user in the same local network. This matches the MAC address of the attacker to that of the user thus giving access to the data or information being exchanged.
-
DNS Spoofing
In DNS Spoofing, the attacker accesses the server and alters the website address record to match his website records thus redirecting the user through the attacker’s website.
Decryption
After the data is intercepted, it needs to be decrypted by creating a two-way SSL traffic. There are many methods an attacker can achieve this:
-
HTTPS Spoofing
The attacker sends a phony SSL certificate containing the digital thumbprint of the user obtained from a compromised application which the browser verifies and approves thus granting access to the attacker.
-
SSL Hijacking
SSL Hijacking can be done when attacker pass false keys to sender and receiver during a handshake. In case, attacker controls the session though it looks like a secure connection between the sender and the receiver.
-
SSL Stripping
In SSL stripping, the attacker downgrades the application or website off it’s SSL encryption through interception and sends the unencrypted version to the user. The user on using the unencrypted version leaves the entire data easily available to the attacker.
How To Stay Secure From Man In The Middle Attacks?
The very outline of MITM attacks work and how they harm the user might make you feel overwhelmed. However, all hope is not lost. It is always possible to ramp up your security and ensure that your data remains secure from interception and decryption.
Here are some ways how you can do it:
-
Look For HTTPS
As a thumbrule, avoid visiting or exchanging information across any websites that do not have the security of HTTPS. If you look for SSL, then you can go with EV SSL that protects you against mimic websites and offers green bar with company name. It is slightly costly compared to other certificate types like Wildcard SSL Certificate, Multi Domain (SAN) SSL, etc.
-
Upgrade System & Server Configurations
Make sure you have the latest version of your server and disable old security protocols versions like SSL 2.0, TLS 1.0. Configure server with proper authentication to secure from MITM attack for example, in Windows server 2008, there is a Network Level Authentication (NLA) that secures against MITM. In case, when the server OS version does not support NLA, you can set mutual authentication by configuring IPSec policies on terminal services that can protect such attack. Besides, you can use VPN as a secure tunnel to prevent MITM attack. It is recommended to use Windows XP SP3 or later in order to take benefit of Network Level Authentication.
-
Avoid Free Public Wifi Hotspots
Don’t fall for the free lunch trap. Free Public Hotspots are hack-prone. Avoid them like a plague. If there is no option but to use them, ensure you are using a Virtual Private Network or a SSL plugin like ForceTLS or HTTPS Everywhere to safeguard your data privacy.
-
Ramp Up System Security
Malware and spyware get installed in a computer when your system is not adequately protected using an antivirus program. Be proactive in renewing your antivirus program and also on conducting regular scans for malware to ensure that no malware is transmitting data to attackers.
Bringing It All Together
According to Netcraft report 2016, 95% of servers have lacking HSTS security feature and are prone to MITM attacks. MITM is fat spreading from desktop connections to mobiles and is even seen to present in the IOT space.
Spyware and malware programs are the prime causes of MITM attacks. MITM attack is carried out in 2 phases: Interception & Decryption. In both the phases, the user is deceived of the true identity of a website or its HTTPS provision and is trapped into broadcasting information publicly.
SSL Hijacking, SSL Stripping and HTTPS Spoofing are some of the common ways attackers deploy to steal information from innocent users.
Using secure private networks, using HTTPS and strengthening security measures are the options left for users to protect themselves from MITM attacks.