As the number of internet users grows exponentially, we also see the dark side of the internet. The number of hacking incidents has been on the rise. Studies show that hackers attack every 39 seconds, and they have been using more sophisticated methods over time. Pharming is one of the means taken by hackers to attack internet users. In this article, we will learn more about it and how we can save ourselves.
What is Pharming?
Pharming is a sophisticated cyberattack that leads the unsuspecting internet user to a fake site instead of a legitimate site. It is usually done to steal your details. Now, when you are trying to visit a site, several activities are undertaken at the back end before seeing the landing page. The hackers manipulate these actions and will take you to a malicious site. The malicious site is mostly a financial or e-commerce site where the details of the user, viz. user credentials, financial information, etc. is taken over usually.
How does pharming work?
It is essential to note how the DNS server works. The DNS servers ensure that the domain names are translated into IP addresses that are the servers’ actual location. The web browser of the visitor connects using the IP address. When you visit a website, the DNS cache is formed, and there is no requirement to see the server every time.
Now, hackers are quite smart to corrupt both the DNS servers and the DNS cache. What can also happen is that a malware may be installed on the computer if the visitor visits a malicious website. The system will be maintaining the cache of previously visited sites while the malware can alter the host files. As a result, the visitor will now be sent to the spoofed website instead of the real one.
An older method is DNS cache poisoning that involves attacking the DNS server itself. The rules that apply to direct traffic to a particular domain are changed. Now the traffic gets redirected to the spoofed website. The DNS hijacking attacks the server itself and can therefore attack several users together.
Types of pharming attacks?
You need to know the types of pharming attacks. They are of two kinds.
Malware-based pharming attacks.
The attackers send a trojan through a malicious email or other means like a lousy application that the user downloads. Once it is downloaded, it gets to work by making its way to the computer’s host file. It starts redirecting the traffic to malicious sites.
It makes you visit the malicious site repeatedly. Even if the malware is removed, you will still be directed to the fake site due to the DNS cache unless you clear the DNS cache. It would be like the original site at the malicious site, and it would be difficult to spot the attack.
Image Courtesy: https://blogvaronis2.wpengine.com/malware-protection/
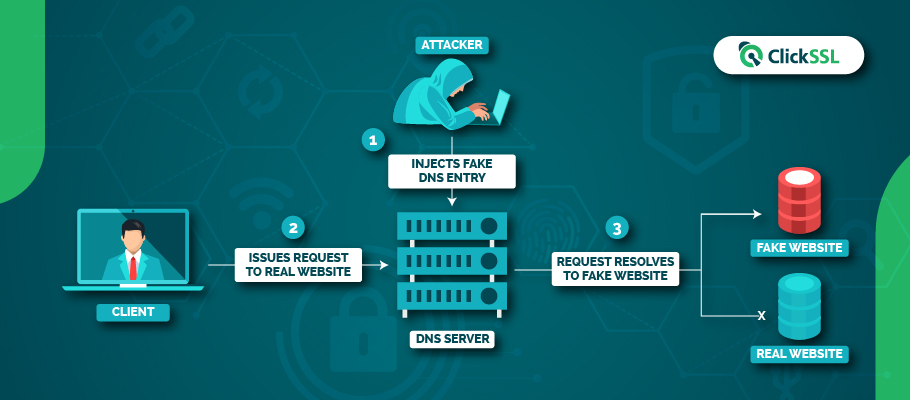
DNS Server Poisoning.
Hackers can also attack the DNS servers directly, allowing them to target a larger number of visitors to the site. They can take advantage of the DNS server’s vulnerabilities to break into it and corrupt the server by sending in fake DNS entries. The legitimate traffic is then redirected to the phony website. This leads to a more massive racket as several thousands of users may get affected.
Pharming Vs. Phishing
It may seem to the layman that both terms are the same. Now, both attacks lead the visitor to a malicious site. So, what is the difference?
A phishing attack involves the user receiving an email that is alluring enough to click on a link and visit the malicious website that resembles genuine. Pharming, on the other hand, does not involve sending any emails or files to the user. You see, the fake website as the hacker has taken over the DNS. The users are unaware of the hacking event as they are not clicking on any link but, maybe, typing the URL themselves.
Ways to secure yourself from the advent of pharming attacks.
It is crucial to check the websites you visit, especially if you visit a financial or an e-commerce website that requires your user credentials. Also, check the website if you intend to do a financial transaction. You must always visit a site that is on the HTTPS platform. There will be a padlock, which means an SSL certificate has been issued to the website. You may click on the padlock and view additional details about the certificate.
Check administrator rights.
You must use your computer with administrator rights when in regular use. It is best to create a separate administrator profile with dedicated rights. It will prevent any hacker from tampering with the host files. Businesses must follow this critically, and all terminals must have a dedicated profile with administrator rights.
Use dependable anti-malware.
A pharming attack is usually undertaken using malware, so the latest anti-malware software version will be helpful. It can block all attempts by hackers to modify the host files on your computer. Most anti-malware applications can work with all operating systems and can also block suspicious websites that may have visited.
A password manager can help.
We generally use a password manager when we have too many websites to visit frequently, and it becomes difficult to remember the user credentials of all of them. It also can help you in another way. The password manager can automatically fill in the user credentials of any website you visit frequently. But, if you are on a malicious site, it will not fill in the details automatically.
Apply Two-factor Authentication.
Most websites allow users to opt for two-factor authentication. The user has to notify a device where a code will be sent, and the user must enter this code to log in to the site. It prevents hackers from gaining unauthorized access even if they have the login credentials.
Conclusion
As we progress technologically, hackers are also using various means to carry on their activities. A pharming attack is one of the standards used by them to meet their nefarious objectives. We must stay on our guard once we know how these attacks are carried out. We have also discussed some of the points on how we can thwart these attacks.
Recommended Reading:
- What is SSL Offloading? Features & Benefits of SSL Offloading
- What is a Digital Signature? Everything You Need to Know
- What is SSL/TLS Handshake? SSL Handshake Explained
- What is Extended Validation SSL Certificates
- What Is Smishing? Everything You Need to Know
- What is Port 443 – What You Need to Know About HTTPS 443