In today’s expanding digital landscape, the significance of secure hash algorithms cannot be emphasized enough. These algorithms are pivotal in upholding the integrity and security of data transmitted via the internet. Notably, three prominent algorithms shine amidst them: SHA-1, SHA-2, and SHA-256.
These algorithms play a vital part in guaranteeing online security, especially in creating and validating SSL certificates. By examining the distinctions between these three algorithms, we gain a deeper comprehension of their collective contribution to fortifying the safety of our online transactions and communications. Despite the increasing threats to our digital lives, the role of these algorithms in protecting sensitive information remains paramount.
What is a Hash Algorithm?
Hash algorithms, or hash functions, are essential mathematical tools in computing. They take an input, referred to as a ‘message,’ and produce a fixed-size string of bytes as output. Each unique input generates a distinct output, regardless of how minor the variation in the input might be, such as a single character change or an entire paragraph modification.
The ‘avalanche effect’ is a critical property of a perfect hash function, where even a small modification in the input results in a dramatically different output, demonstrating a lack of correlation with the original hash value.
Hash algorithms are of utmost importance in contemporary computing, particularly for data encryption and security purposes. They find extensive applications in data retrieval, password storage, data integrity verification, and digital signatures.
Examples of secure hash algorithms (SHA), including SHA-1, SHA-2, and SHA-256, exemplify cryptographic hash functions that effectively safeguard the security and integrity of data transmitted through the internet.
A crucial feature of secure hash algorithms is their one-way nature. They can take input data and produce a hash, but it is not feasible to retrieve the original input data from the hash. This property makes hash functions invaluable for data security purposes.
How Hashing Algorithms Fit Into SSL/TLS
Hashing algorithms are vital for SSL/TLS protocols, ensuring secure internet communications. These algorithms maintain data integrity and authenticity during transmission.
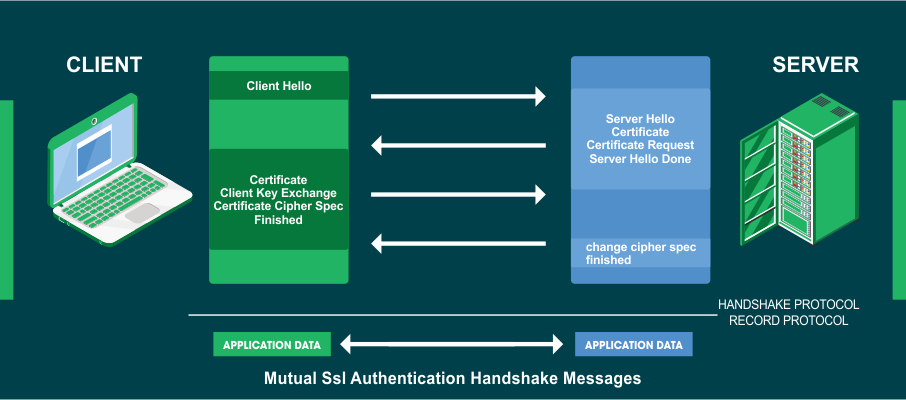
Establishing an SSL/TLS connection involves a crucial process known as the ‘handshake.’ During this process, hashing algorithms are pivotal in generating and validating digital signatures. These signatures are imperative in affirming the identities of the parties engaged in the connection.
Let’s delve into how this process unfolds:
1. The sender creates a digest of the message using a hash function.
2. The sender then encrypts the digest with their private key, generating a digital signature.
3. The recipient receives and decrypts the signature using the sender’s public key.
4. Next, the recipient applies the same hash function to the received message, producing another digest.
5. Finally, the recipient compares the two digests. If they match, the message is considered authentic.
In summary, during the SSL/TLS connection setup, the handshake process employs hashing algorithms to create and verify digital signatures, ensuring the authentication of the parties involved.
Furthermore, hashing algorithms are also instrumental in generating and validating session keys during the handshake process. Incorporating secure hash algorithms into SSL/TLS protocols is of utmost importance in safeguarding the confidentiality, authenticity, and integrity of online communications.
The handshake phase involves the exchange of a pre-master secret, from which a secure hash is derived. This hash forms the basis for generating symmetric session keys, which are vital for encrypting and decrypting transmitted data. Consequently, unauthorized access is thwarted, data authenticity is ensured, and any attempts at tampering are prevented.
Difference Between SHA-1, SHA-2 and SHA-256
SHA1
SHA-1, officially known as Secure Hash Algorithm 1, is a meticulously devised mathematical tool created by the United States National Security Agency (NSA) in 1995 with a strategic mission to fortify digital data security. Think of it like a unique fingerprint for data. It takes any information, like a document or a message, and churns it through its mathematical magic, producing a fixed-length sequence of numbers and letters like a secret code. This sequence is called a hash value.
SHA-1 gained popularity because it was fast and easy to use, finding its way into various security systems, like when you see the “https://” in your web browser. It made sure your data stayed tamper-proof and secure. But, as technology evolved, so did cyber threats, and SHA-1 started showing weaknesses. Crafty hackers found ways to crack its code, making it less secure.
While initially deemed secure, SHA-1 faced challenges as vulnerabilities were discovered over time. In 2005, cryptanalysts found a significant concern in the form of a collision attack, where two different inputs produced the same hash value. The apprehensions concerning SHA-1’s capacity to withstand collision attacks and uphold cryptographic integrity were significantly amplified.
To mitigate these vulnerabilities, the industry progressively eliminated the utilization of SHA-1 and adopted more robust alternatives, such as SHA-2 and SHA-256. Leading web browsers significantly bolstered this critical transition, which actively alerted users to websites that persisted in employing SHA-1 SSL/TLS certificates.
This move ensured better online communications and transactions security, reinforcing the commitment to safeguarding sensitive data and upholding the highest information protection standards.
SHA-1 has lost its status as a secure cryptographic solution due to its intrinsic vulnerabilities. Consequently, organizations and developers are strongly advised against integrating SHA-1 into any new software, especially for projects involving sensitive data or critical security systems.
SHA2
SHA-2, or Secure Hash Algorithm 2, represents a distinguished family of cryptographic hash functions meticulously crafted by the United States National Security Agency (NSA) in 2001. Its inception aimed to augment the security of its predecessor, SHA-1, which had been found to harbor certain vulnerabilities. With its meticulously crafted design and relentless pursuit of improvement, SHA-2 has undeniably established itself as the paramount cryptographic standard in the industry. Widely embraced and respected, it offers unparalleled safeguards for data transmitted over the internet.
The SHA-2 family has six strong hash functions: SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, and SHA-512/256. SHA-256 and SHA-512 offer 256-bit and 512-bit hashes, respectively, surpassing SHA-1’s 160-bit output. This significant enhancement ensures a higher level of security and protection.
Unyielding in its robustness and resistance to collision attacks, SHA-2 has solidified its position as the definitive industry standard for cryptographic applications. From SSL/TLS certificates to digital signatures and data encryption, SHA-2’s versatility is pivotal in fortifying online communications, guaranteeing data authenticity, and safeguarding sensitive information.
The true strength of SHA-2 lies in its remarkable ability to consistently generate unique hash values, even in the face of minor alterations in input data. This exceptional feature cements its reputation as an unparalleled cryptographic solution, deserving of its esteemed status.
This distinctive avalanche effect guarantees that even slight changes in the input result in entirely different hash outputs, instilling supreme confidence in data integrity verification.
Given its widespread acceptance and proven security, SHA-2 has rightfully earned its place as a cornerstone of modern cryptography. This technology significantly guarantees the safety and confidentiality of digital transactions and communications, reinforcing our defenses in the continuously evolving cyber landscape of the contemporary era.
SHA256
SHA-256 constitutes a fundamental component within the SHA-2 cryptographic hash function series and originates from the United States National Security Agency (NSA), representing a notable enhancement over its predecessor, SHA-1. It has since become widely trusted and used in modern cryptography.
SHA-256 takes input data and generates a fixed 256-bit hash value, a 64-digit hexadecimal string. This hash value serves as a digital fingerprint, ensuring data integrity. Even the smallest input change results in a significantly different hash output, showcasing SHA-256’s avalanche effect, a crucial property for cryptographic use.
SHA-256’s collision resistance makes it vital in security, especially in cryptocurrencies like Bitcoin, for transactions and proof of work. It’s widely used in SSL/TLS, digital signatures, password hashing, and data encryption. Its strength lies in providing high-level security, and safeguarding data confidentiality and authenticity in online communications and transactions.
However, the continuous advancement of technology poses an ongoing challenge to cryptographic algorithms. Cryptographers and security experts closely monitor SHA-256’s performance and research to ensure it remains resilient against potential future threats.
Conclusion
Secure hash algorithms play a pivotal role in upholding the integrity and security of data in today’s expanding digital landscape. Among the prominent algorithms, SHA-1, once popular, is now deemed insecure due to vulnerabilities exposed over time. In its place, SHA-2 emerged as a highly esteemed cryptographic standard, with SHA-256 standing out as the most widely embraced variant.
Its robustness and resistance to collision attacks make it a cornerstone of modern cryptography, ensuring the safety and confidentiality of digital transactions and communications. As technology advances, continuous monitoring and research on SHA-256’s performance remain essential to maintain its resilience against future threats in safeguarding our sensitive information online.
Recommended Reading: