Data security is extremely pivotal in this digital world. Not only does it ensure business integrity, but it also helps maintain customer trust and loyalty. All this can be achieved by ensuring strong data security solutions, of which encryption security solution tops the list.
This article will discuss what is encryption, its importance and its types in the digital world.
What is Encryption?
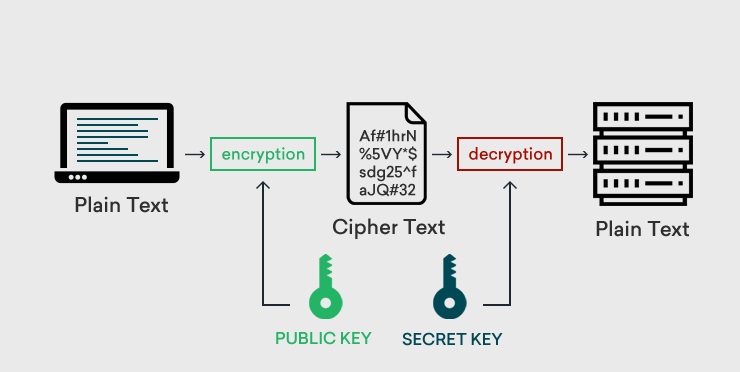
Encryption is an essential cyber security solution that prevents data from being modified, compromised, or stolen. It is the method wherein the sensitive information is masked by encryption algorithms and is converted into a cipher form. This cipher text looks like a coded text and can be decoded with a secret key (comprising decode algorithms) which lies with the intended recipient.
In short, the critical data stays hidden and is inaccessible to intruders. Client-server communication is secured in such a way that even if an intruder gains access to critical data, they cannot read (decode) it and hence can’t misuse the same.
Why is Encryption so Important?
Nowadays, businesses are becoming digital since they can reach out to the masses. Having a business website is common in the modern world. These websites are storages of customer information and other business-sensitive data.
This must be safeguarded to ensure the business’s reputation and imbibe customer trust. Encryption helps fulfill this purpose by providing secure exchanges between the client and the server. Data confidentiality is established, and intruder access is prevented by encryption.
#1. Data Integrity:
As stated above, encryption ensures that intruders and unauthorized personnel don’t modify the data during the exchange process or in storage. Thus, data integrity is maintained since it is transmitted to the recipient in its original form.
#2. Data Confidentiality:
The transmitted data is coded, so data confidentiality is maintained. Encryption also blocks malicious intruders from accessing the data in transit or storage.
#3. Data Security
Encrypted data stays secure in all situations, i.e., even when an intruder has gained access, the data cannot be decoded without its proper key.
In cases where the device is stolen, the data is still secure, which prevents data breaches.
#4. Verification:
Encryption is a stamp that verifies that the customer data will be safe and that the site data is original. Even during data access, the user’s browser can verify that the site they are approaching is genuine.
#4. Regulations:
As per PCI DSS (Payment Card Industry Data Security Standard) or Health Insurance Portability and Accountability Act (HIPAA), encryption is compulsory for e-commerce industries, banks, financial institutions, healthcare industries, etc., where customer data is exchanged or exchanged or exchanged stored.
In short, encryption is important for secured communication exchange and for keeping unwanted intruders at bay.
How does Encryption Work?
Encryption security works on the Encode/Decode Formula.
Encryption security uses an encryption key to encode the pain text into ciphertext. The same is carried out with the help of cryptographic algorithms. This encrypted text is later decoded in its original form by the recipient of the message with the help of a decryption key.
These encryption/decryption keys are unique and are created with algorithms. The concept for the keys is that the longer the cryptographic key, the harder it is to crack the code.
Secured encryption methods use a 256-bit encryption key for data privacy. This can neither be guessed by an intruder nor calculated by a computer, thus preventing successful brute-force attacks.
Encryption Example:
Plain Text: “My name is Jack”
Ciphertext: “fwedeji2j0wfjkeiw93dke”.
The sender will encrypt the message with the encryption key, and the receiver will decrypt the same with the decryption key. Modern cryptography uses thousands of characters (strings) to make these keys to keep them unique and secure.
Note: Encryption is the key for Hypertext Transfer Protocol Secure (HTTPS) since it establishes secure communication between a browser and a server.
Encryption HTTPS can be gained by installing SSL/TLS certificates on sites to ensure data integrity.
What Are the Types of Encryptions?
There are two types of encryptions.
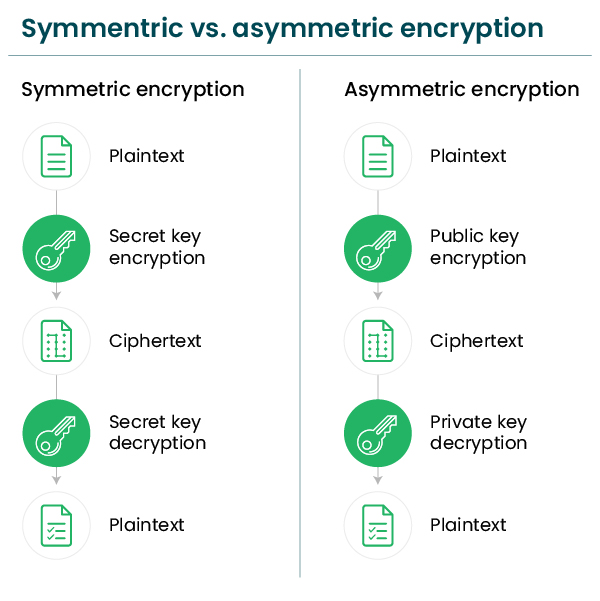
#1. Symmetric Encryption:
Symmetric encryption uses a single key for the encryption/decryption process, i.e., the keys for encrypting and decrypting the data are the same. Only one key is used for securing data exchanges between the browser and the server.
The symmetric keys can be easily generated and are inexpensive since less computing power is needed. The process of encoding/decoding is quicker in symmetric encryption.
The only drawback is that sharing the key becomes risky because if the key falls into the wrong hands, the intruder can access, decrypt, modify or send messages to other parties.
#2. Asymmetric Encryption:
Asymmetric encryption is also termed PKI (public-key cryptography), which uses two different keys for the encryption/decryption process. They are the public key and the private key.
The public key is shared publicly amongst all who want to send encrypted messages. On the other hand, the private key lies with the intended recipient since they have the sole right to decrypt these messages. This encryption is more secure than symmetric encryption.
The only drawback is that this encryption is slower and more expensive than the former since it needs more computing power to create the keys.
Common Encryption Algorithms:
Common encryption algorithms of Symmetric Encryption include:
Data Encryption Standard (DES):
The DES, developed in 1970 and implemented in 1977, only used a key size of 56 bits, which was quite insecure. Hence this algorithm became obsolete in the modern era. But it still had a great and powerful contribution to modern cryptographic development.
Triple DES (3DES):
To overcome the insecurities caused by the DES algorithm, 3DES was introduced. As the name states, it applied the DES algorithm thrice to each block for strong security.
But, 3DES is too considered insecure and was lamented in 2017.
Advanced Encryption Standard (AES):
AES was implemented in 2001 and is the most popular encryption method. This encryption algorithm uses a block size of 128 bits and key sizes of 128, 192, and 256 bits. It encrypts each block and later joins them to create a cipher text.
Since AES now uses a key length of 256 bits, brute force attacks also fail to break the encryption security, thus making it the most powerful encryption algorithm in the digital world.
Twofish:
Twofish is used for both hardware and software. This symmetric block cipher uses a block size of 128 bits and a variable-length key of sizes 128, 192, or 256 bits. This is a strong encryption algorithm, but it works better on text encryptions than image encryptions.
Common encryption algorithms of Asymmetric Encryption include:
Rivest-Shamir-Adelman (RSA):
RSA is the acronym of Rivest-Shamir-Adelman. The surnames of the creators of this algorithm are used to name this algorithm. This trio publicly described this algorithm in 1977.
This encryption algorithm is widely used in various products and services, specifically in SSL/TLS certificates, wherein it’s used for digital signatures and to establish a secured communication tunnel for data exchange.
The RSA public key can be used by many, but the private key for decrypting the message, as stated before, lies with the recipient of the message only.
Elliptic Curve Cryptography (ECC):
This technique is based on elliptic curve theory over finite fields. ECC is an alternate algorithm of RSA and creates quicker and smaller cryptographic keys, which are more efficient for securing data.
Example: A public key (256-bit elliptic curve) is almost as good as a 3072-bit RSA public key.
This algorithm provides such strong security keys and is generally used for digital signatures in emails, cryptocurrency (Bitcoin, Ethereum, etc.) software, and data.
Encryption Best Practices:
Some of the data encryption best practices include:
Keeping your Private Key Secure:
If the key falls into the wrong hands, it can damage your business reputation and create havoc. Store the encrypted key on an external device and keep it safe.
Limit user access, and if the key is stored on your device, ensure that it is stored in a secured folder.
Encrypt all Data:
It’s wise to encrypt all the information rather than focus on sensitive stuff. This will prevent hackers from breaching your systems and data.
Assess Data Encryption Performance:
Assess the encryption performance and ensure that it’s effective in terms of utilization of resources. It shouldn’t load your CPU and should not be time-consuming. If this process is slow, consider moving to another algorithm.
Prepare a Backup Strategy:
You should have a rock-solid backup strategy in unwanted situations like theft, back up your files and folders where the decryption key is stored and place the backup in a different location.
What Is the Difference Between a Public Key and a Private Key in Encryption?
Some of the key differences between the public key and the private key are:
Use:
The public key is used for the Encryption of data.
The private key is used for the Encryption and decryption of data since its shared by both parties in symmetric Encryption.
Performance:
The public key’s mechanism is slow compared to the private key.
Secrecy:
The public key is available to the public for encryption purposes.
The private key is kept secret and lies with the intended recipient only.
Type:
The public key is used in asymmetric Encryption since two keys are used in the encryption/decryption process.
The private key is used in symmetric Encryption as a single key is used in the encryption/decryption process.
Conclusion for Encryption
Encryption is a vital tool for maintaining data integrity and data privacy. In this digital world, where hackers are outsmarting IT developers and cybersecurity solutions, encryption security is an intrinsic tool for maintaining data confidentiality, email privacy, and transaction security.
All the digital data stored or transmitted on the internet needs encryption security to prevent intruder access and misuse.
Approach a reliable SSL certificate provider, and install an SSL certificate on your server to avail the benefits of encryption security to secure your digital empire.