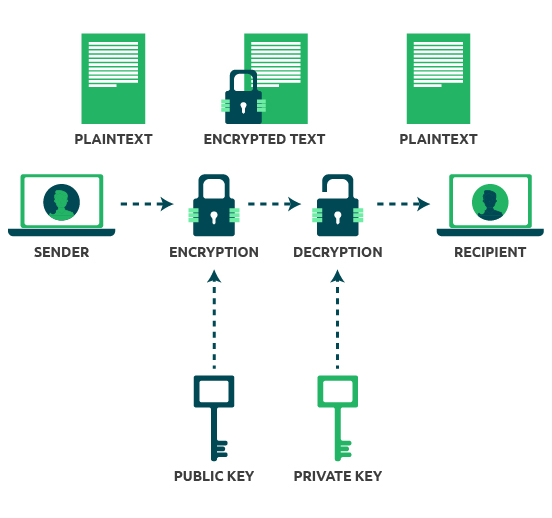
Public key encryption is a cryptography method that leverages two different keys, known as keypair. The private key is kept separately and the other; the public key is shared publicly. However, both keys are closely related to each other. Only the private key can decrypt the data encrypted by the public key.
Usually, the public key is only leveraged to encrypt the data, and the private key is used to decrypt the data. This encryption method is leveraged all over the world by leading digital applications and organizations to ensure the safe and secure exchange of messages and files.
In this article, we are going to discuss about “public key encryption”. Let us dive into the details.
What is Public Key Encryption?
Public key cryptography is used to sign data with two different keys public and private keys. The public key encrypts data while the private key decrypts data. A Public key is available to everyone. On the other hand, a private key should be kept secretly to avoid unauthorized access.
How Does Public Key Encryption Work?
Public key encryption allows users to deliver messages secretly to anyone who has published their public key, and only the recipient can decrypt the message. This way, a secure system to exchange messages is set up safely.
Public key encryption allows each user to create a public key and a private key. Both the keys are connected to each other through very large numbers that have mathematical properties. The system decrypts the encrypted message sent by another user by matching the public key of the user with one’s private key.
Here are the essential characteristics of a public key encryption system:
- Separate keys are used for both encryption and decryption of the data.
- Every message receiver has a unique decryption key. In common terms, it is known as the private key.
- The key published by the receiver is known as the public key.
- Public key can be shared among users to allow anyone to encrypt the message and authenticate the digital signature. While the private key is kept secretly and only the holder of the private key can decrypt the message along with creating digital signature.
- It is practically not possible to determine the decryption key but only given knowledge of the cryptographic algorithm and encryption.
Strength of Asymmetric Keys
Symmetric keys are considerably longer than asymmetric keys. However, they also come in three different categories, and the length of its key identifies the strength of each asymmetric encryption.
- High Strength Asymmetric Key – 4096 bits
- Medium Strength Asymmetric Key – 2048 bits
- Low Strength Asymmetric Key – 1024 bits
Is Public Key Encryption Better?
Also known as asymmetric encryption, it encrypts the data asymmetrically. Hence, the data encrypted by asymmetric encryption is more difficult to crack than the same data encrypted by symmetric encryption.
However, the security of asymmetric keys cannot be gauged by their length. Key metrics, including ease of distribution and computational burden, play a vital role in creating a highly secure key.
Symmetric encryption uses the same key for encryption and decryption. Hence, if you need to send the symmetric encryption key to the receiver through the internet, then you can’t guarantee bulletproof security of your data as anyone can gain access to the key.
While asymmetric encryption doesn’t require the sender to share the same key with the receiver. This means that if the user’s private key is safe, there is no need to worry about data security.
Aside from this, the user can distribute the public key without having to worry about the recipient of the key. The owner of the public key can encrypt the data, but only the owner of the private key can decrypt the data.
How Does TLS/SSL Use Public Key Encryption?
TLS/SSL (Transport Layer Security/Secure Socket Layer) is a security protocol that is leveraged to facilitate encrypted communication over a network. It is a crucial security layer for any website that plans to implement an absolute data security framework. It uses public-key encryption, also known as asymmetric encryption. The security protocol uses Public & Private Keys (PKI) to leverage a flexible encryption scheme.
Apart from asymmetric cryptography, these protocols also take advantage of the X.509 certificate to authenticate users with whom they are connected and exchange keys securely. TLS/SSL is leveraged to apply absolute integrity, confidentiality, and secure authentication of keys.
Here is How It Works With the Public Key Encryption:
#1. Server Authentication
The client leverages the public key of the server for data encryption. The server can generate the secret key if and only if it can accurately decrypt the data with the right private key.
#2. Client Authentication
The user can leverage the public key present in the client’s certificate to decrypt the data that the client pings as a random data byte with the client’s digital certificate and the private key. Then the TSL to TLS pings the server with a ‘finished’ message encrypted with the secret key. The same message is also sent to the client. The session terminates if any of the authentication steps fail.
Digital certificate exchange during TSL or SSL handshake is a crucial part of the authentication process.
How TLS/SSL Deliver Confidentiality?
SSL and TLS leverage public key encryption to ensure end-to-end security of data. During the SSL/TLS handshake, the SSL/TLS server and client decide an encryption algorithm along with a shared secret key that is used for only one session.
After this, all the messages exchanged between SSL/TLS client and server are completely encrypted through the key and algorithm. This practice ensures the complete privacy of messages even when they are intercepted by malicious forces.
Absolute privacy is possible because SSL/TLS leverages public-key encryption in which there is no need to distribute the keys, and the receiver’s private key decrypts the message.
Summery for Public Key Encryption
In today’s age of cybersecurity, where all kinds of personal and professional information are over the internet and data has become the prime target of every hacker, it has become crucial to have end-to-end data security systems in place.
Public key encryption has emerged as a boon for software vendors to ensure absolute privacy and integrity of data. When leveraged in the right manner, it can keep you safe and secure from all kinds of data security threats looming all over the world.
Recommended Reading: