Symmetric vs Asymmetric Encryption – In a simple word Asymmetric encryption is more secure than symmetric encryption.
Data integrity is a sensitive aspect of any organization. When planning your course of work for the future, you must focus on reliable measures of safeguarding your confidential data from unauthorized access and fraud anywhere during the data cycle.
One of the foolproof ways of achieving this is through data encryption. It refers to a series of encoding of confidential data in a way that only the individuals that are authorized by the company can access it.
In encryption schemes, there are two techniques you can employ to ensure data security i.e., Symmetric encryption and Asymmetric encryption.
The primary difference between these two types of encryption is that, with Symmetric encryption, the message to be protected can be encrypted and decrypted using the same key.
Asymmetric encryption, on the other hand, requires the use of two separate keys i.e., a public key and a private key.
In this case, data can be encoded by the public key, whereas data can be decoded by the private key.
Before we decode the difference between Symmetric vs Asymmetric Encryption, Let’s learn about Symmetric and Asymmetric.
What is Asymmetric Encryption
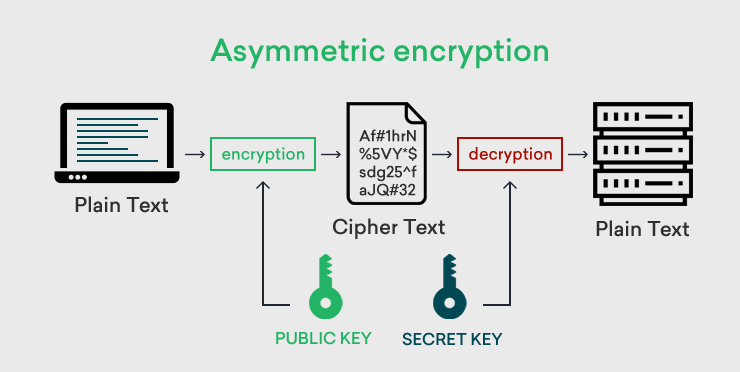
Asymmetric encryption is an encryption model that requires two keys, for example, Key A and Key B. It works in such a way that the information that Key-A can encrypt while Key-B can decrypt.
Usually, these keys can be used interchangeably such that if you use Key A to encrypt data, you can use Key B to decrypt this information, and if you use Key B to encrypt information, you can decrypt the same information using Key A. This is however not fundamental in Asymmetric Encryption.
Now, if you wish to use Asymmetric encryption, you will have to create a pair of matching keys. After that, you’ll make the encryption key public and the decryption key private hence the name public-key cryptography and private key cryptography.
You can then sign private messages by encrypting them using the public keys. This is important because it ensures that only the intended recipient with the matching private keys of the messages can see them and not a would-be interceptor.
For the best experience using Asymmetric encryption, you will need a key management system using Public Key Infrastructure to ensure that the public keys stay safe and reliable.
Before we decode different Symmetric vs Asymmetric encryption, let’s learn about Symmetric and Asymmetric.
Asymmetric Encryption Use Cases
Digital Signatures: Digital signatures help detect malicious data modifications and authenticated signatory identities. Besides, they can also be used by signed data recipients as proof that the signatures are from the intended signatories. This activity is known as repudiation.
Now, the digital signatures used here work on Asymmetric cryptography and provide an extra layer of security to messages that are delivered via insecure channels.
What is Symmetric Encryption
Symmetric encryption is a data encryption model that works with just one key for encrypting (encoding) and decrypting (decoding) private data. It’s a popular encryption option, and the secret key used here can either be a mix of letters, words, or numbers (look like gibberish characters).
For it to work, both the recipient and sender must know the private key to use for encoding and decoding data. It works by encrypting plain text then converting it to ciphertext with the help of an encryption algorithm and private keys.
The ciphertext can then be converted again to plain text with the help of the private key that was used to encrypt it with the decryption algorithms.
Symmetric Encryption Use Cases
#1. Banking Sector: The high speed and swifter execution functionalities makes symmetric cryptography a preferred option for encrypting bulk data in the banking sector’s areas like;
- Validations to ensure that messages coming in are from the intended senders.
- Payment applications e.g., the transactions involving payment cards where the Personal Identifying Information (PII) must be protected to avoid fraudulent charges or identity theft without expensive investments in resources.
#2. Data at rest: Symmetric cryptography is also widely used to secure data stored in hard drives, archives, computers, flash drives, and laptops. These are data that are not involved in the active movement from network to network or device to device.
To protect such data, you can encrypt all the confidential files before storing them or encrypt the entire storage drive.
This table compares the significant differences between Symmetric encryption and Asymmetric encryption.
Difference Between Symmetric vs Asymmetric Encryption
Symmetric encryption uses a single key for encryption and decryption while asymmetric encryption uses two different keys for encryption and decryption.
| The Basis for Comparison | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| The Number of Cryptographic Keys Used | It requires just one key to help with both encryption (encoding) and decryption (decoding) of confidential data. | Requires a pair of matching keys i.e., public and private keys, to help with encryption and decryption purposes. |
| The Primary Purpose | Symmetric Encryption is mostly required when dealing with the transmission of bulk data. This is because it’s quicker and easy to execute. | Asymmetric Encryption is a viable option if you only wish to get a secure environment for exchanging your secret keys. This is because of the complexity it has in execution and the slow speed in using it. |
| The Algorithms Used | Symmetric encryption uses these algorithms;
|
Asymmetric encryption uses the following algorithms;
|
| Ease of Use | Requires just one key hence very easy to use. No matching keys required for decrypting the encrypted data. | It requires both public and private keys, which must match for you to decrypt information. This makes it a bit difficult to use. |
| Performance | Simple in nature and easy to execute. Very swift. | There must be a pair of matching keys for it to work. Besides, comparing these keys can be a bit time confusing, making it another work on its own. |
Symmetric VS Asymmetric Encryption Use Cases
#1. Messaging Apps
Popular messaging apps like WhatsApp and Signal rely on end-to-end encryption to help safeguard the privacy and confidentiality of communications on the platforms and also in authenticating users. The end-to-end encryption used here helps keep the messages out of reach of unauthorized third parties and even the messaging vendors themselves.
The end-to-end encryption technology here uses both symmetric and asymmetric encryption to safeguard the message during transit and initialize encrypted conversations.
#2. Public Key Infrastructure
In public key infrastructure, both encryptions are used like asymmetric and symmetric cryptography. Asymmetric encryption is applied to create connections then symmetric encryption will replace asymmetric encryption. Both types of encryption tasks named as public-key cryptography, which is used to create a secure connection on the public internet.
All HTTPS connections between clients and servers use both Asymmetric and Symmetric encryption, whereby Asymmetric encryption is used in establishing connections and then replaced by Symmetric encryption for the entire connection duration, which is also known as the session.
Google recommends that you switch to HTTPS or it will scare off your visitors with insecurity warnings. HTTPS is focused on machine identification.
Wrapping Up
Usually, there are pros and cons to each encryption method. However, symmetric encryption uses only a single key to encrypt and decrypt for data encryption hence, there are chances that hackers can intercept the session. In asymmetric encryption, both keys are used for encoding and decoding so, from a security point of view, asymmetric encryption is reliable.
Related Post: