SSH vs SSL – SSH is used to create a secure connection between two computers to issue commands and transfer data, while SSL secures the data transfer between the browser and server.
SSH allows encrypted data between two computers connected on an open network like the internet. SSH allows network administrators to run commands and move files from one computer to another computer.
On other hand, SSL does allow the data transfer from a user’s browser to the server where the site is located. There is no need to run a command. Once you install SSL, a secure connection is established for encrypted data transfer.
If you have not installed an SSL certificate, the data remains in plain text and the third person can see and modify the details. Such data travels with HTTP protocol instead of the secured HTTPS protocol.
We will be looking into the differences and similarities of SSH and SSL, SSH vs. SSL, and it will help you decide which one to choose in the end.
SSL: The Bedrock of Web Security
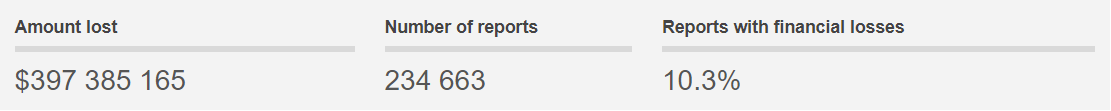
The internet has made the lives of people more comfortable, and it is mostly a boon for businesses. But there are setbacks of using the internet as well. If you take a look at the scam statistics, in 2023 alone, people have lost $397 385 165 in different scams.
And the list of the top 10 scams includes online shopping scams.
No wonder people trust only reputed businesses and hesitate to make connections with new companies. If you are new online, you will need to create an environment that will make your clients trust you.
This is where SSL (Secure Sockets Layer) certificates come in. It is an online security protocol that offers data encryption, thereby assuring your visitors that their connection is secure.
When you install an SSL certificate like EV SSL Certificate, it will provide visual cues in the form of a
#1: Secure Padlock
#2: Secured URL with your organization or business name
#3. And a trust seal
These visual cues will make people trust your business more.
Functions of SSL/TLS
The main functions of SSL/TLS are:
#1. Data encryption
Data encryption core function is to safeguard server-client communication. Thus, it encrypts every bit of information or data which can only be unlocked by the intended recipient. This SSL feature is excellent if your website holds sensitive data such as IDs, passwords, payment information, etc.
#2. Authentication
SSL certificate provides authentication to your website by requiring you to undergo an identity verification process. A genuine Certificate Authority won’t issue an SSL unless you complete the thorough validation processes. Thus, people will trust your website, as it has been run by a genuine person and not a scammer.
How SSL/TLS works?
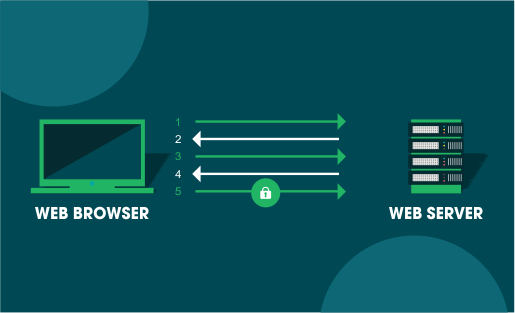
After you install an SSL on your website, whenever a browser tries to access it, the browser and the webserver form a connection by a process known as an “SSL Handshake.” This process is not visible to the user.
Three keys are utilized while setting up the SSL connection:
- Public key
- Private key and
- Session key.
When the data is encrypted via the public key, it can be decrypted using only the private key, and vice versa.
When a secure connection is made, all transmitted data is encrypted using the session key.
Uses of SSL/TLS in Data Security
You can use SSL/TLS to secure:
- Online credit card transactions and other online payments.
- Intranet-based traffic, for instance, file sharing.
- Extranets and database connections.
- Webmail servers.
- Office communication servers.
- File transfer, for instance, when you update new pages to your website or transfer large files.
- System logins to apps.
- Control panels.
- Workflow, and more.
SSH: A Method to secure Remote Communication
The SSH protocol (Secure Shell) is a method that secures remote communication from one computer to another. It provides strong authentication while securing communications and integrity via encryption.
This security protocol is usually used to access Unix-like operating systems. However, you can also use it on Microsoft Windows.
Functions of SSH
#1. Encryption
SSH offers three types of encryption to secure communications:
- Symmetric encryption: In this form of encryption, a secret key is used while encrypting and decrypting a message by both the client and the host.
- Asymmetric Encryption: In asymmetric encryption, two separate keys are used for encryption and decryption, called the public key and the private key. These keys form a public-private key pair.
- Hashing: SSH also uses one-way hashing, a form of cryptography that cannot be decrypted. A unique value of a fixed length is generated for each input that shows no clear trend, making them practically impossible to reverse.
#2. Authentication
Another function of SSH is to provide authentication. Made up of three different protocols, namely, the transport layer, the authentication layer, and the connection layer, together, these protocols authenticate the other party in the connection. It encrypts data and provides confidentiality while checking the integrity of the data.
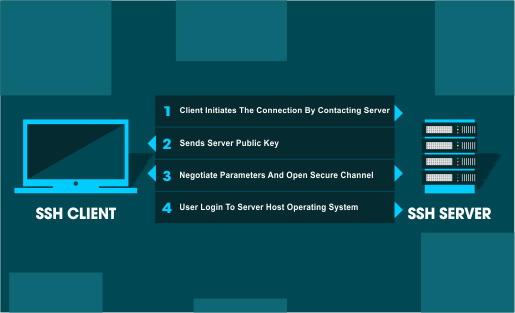
How does SSH work?
In SSH, the connection is established by the SSH client attempting to connect to the SSH server. In the process, the client utilizes public-key cryptography to authenticate the SSH server’s identity.
When the setup is done, the SSH protocol will implement strong symmetric encryption and hashing algorithms to safeguard the data’s privacy and integrity that is exchanged between the client and the server.
Uses of SSH in Network Security
The uses of SSH in network security include:
- Protected remote access to network systems enabled by SSH.
- Safe file transfer sessions.
- Automated and protected file transfers.
- Giving out secure commands on remote devices or systems, and
- Managing network infrastructure components securely
SSH vs. SSL/TLS: The difference between
You can easily differentiate SSH and SSL by these traits:
- SSH implements port 22 while SSL utilizes port 443.
- SSH can help you execute commands across the internet securely while SSL can transmit critical information like payment information securely.
- SSH requires a password authentication system while establishing a secure connection. SSL doesn’t need it.
- SSH primarily deals with network tunneling while SSL deals with certificates.
SSL vs. SSH: A side-by-side comparison
SSH and SSL are comparable in that they’re both PKI based. Moreover, both SSL and SSH encrypts communications and needs authentication. But while SSL transmits information, SSH is used to execute commands.
So, SSH vs. SSL: Which security protocol should you use?
It depends on the type of security you want.
You can use SSL to secure internet connections between the client and the server. It is excellent for providing security to clients while conducting online business transactions.
SSH is used to run commands via remote access. If you are a network administrator, you can use it for managing systems and apps remotely. It will enable you to log in to another system over a network, execute commands, and transfer files from one system to another.
Related Post: