The tremendous usage of the internet by people all across the globe has invited hackers to our networks, who try to invade the privacy and confidentiality of the data, thus challenging digital security solutions.
Research by Cybersecurity Ventures indicates that the growth of cybercrime is expected to reach USD 10.5 trillion by 2025, up from USD 3 trillion in 2015.
Many security tools are available in the market. One such encryption and decryption term of cryptography is termed “keys.”
Encrypted information, digital certificates, digital signatures, etc., are examples of cyber securities that rely on a secret key termed the cryptographic Private Key.
What is a Private Key?
In cryptography, a key is a string of characters randomly used in an encryption algorithm for scrambling/unscrambling data. These keys are unique and non-predictable since algorithms create them.
A Private Key (Secret Key) is a cryptographic key used to encrypt and decrypt data. This key must be stored in a secured place, and its access should be given to the concerned parties only, i.e., the sender and the receiver of the message. These parties use this key for encryption and decryption of the message, respectively.
These keys are used in symmetric and asymmetric encryptions and in cryptocurrencies.
How the Private Key is Mathematically Different from Public Key?
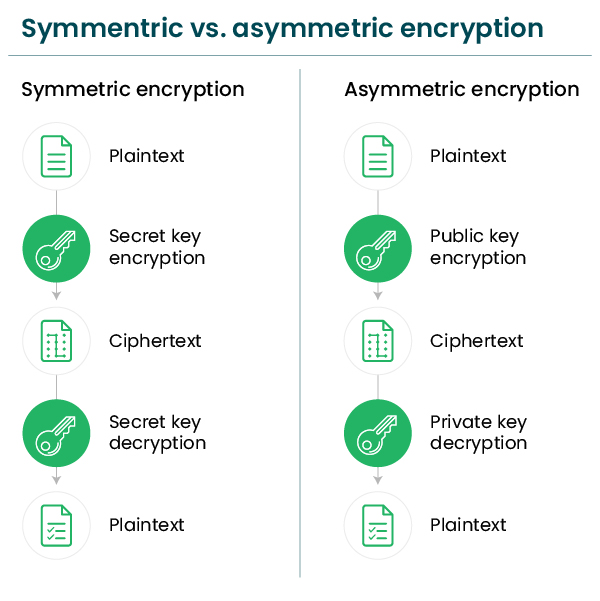
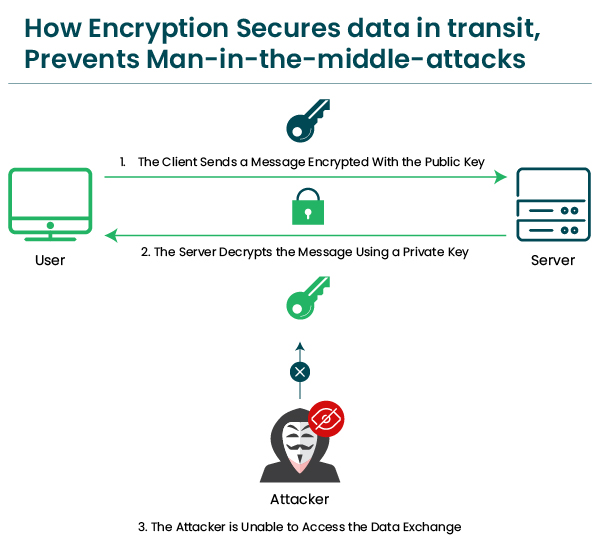
The private key is used in sync with the public key, i.e., the public key is used by the sender to encrypt the data, whereas the intended recipient uses the private key to decrypt the data. This pairing of the private (secret) and public key helps perform the encryption/decryption process.
Though the private key is mathematically linked to the public key, it differs in a few aspects.
Secrecy
The private key is stored in a secret location, and only the intended recipient can access it.
The public key is publicly available to all who want to encrypt the information; hence, it need not be kept secret.
Usage:
The private key is used in asymmetric and symmetric encryption.
The public key is used in asymmetric encryption only.
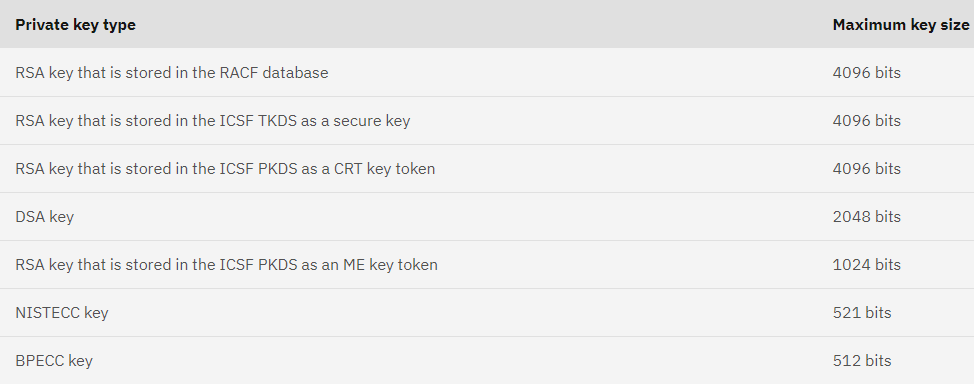
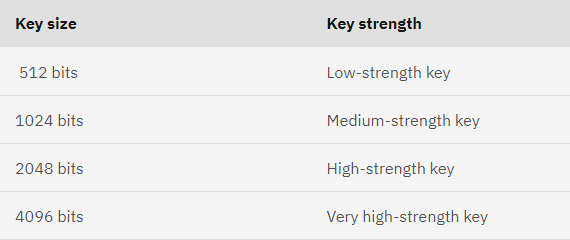
Length of the Private Key:
A DSA key size is 512, and the minimum RSA key is 512-bit. The token key data set (TKDS) refers 1024-bit RSA key size, which should be a multiple of 256 numbers. The United States export regulations have the authority to decide the key size.
RACF and non-RACF codes control the key size regulation.
The maximum private key size depends on the key type. Check out the below-mentioned image.
Presently, the regular RSA key sizes are shown in the below image.
Private Key Vs. Public Key
| Key | Private Key | Public Key |
| Algorithm | This key is used for the encryption and decryption of information. | This key is only used for encrypting data. |
| Sharing | This key is shared with the sender and receiver of the encrypted data. | This key is only shared with the sender of the data. |
| Speed | The speed of the private key is faster than the public key. | The speed of the public key is slower than the private key. |
| Secrecy | This key is kept secret and only the sender and the receiver have an access to it. | This key is shared amongst all the senders (public) who wish to send a message. Only the private key is kept a secret. |
| Symmetry | It is used in symmetric encryption, where only one key is used in the entire process. | It is used in asymmetric encryption since two keys, i.e., the private key and the public key are used in the entire process. |
| Efficiency | It’s more efficient. | It’s less efficient. |
| Capacity | It’s ideal when large texts need to be secured. | It’s ideal for securing short texts and messages. |
| Key Loss | There are chances of key loss since the key is stored on the server. | There are no chances of key loss since the key is accessible publicly. |
Keep Your Private Key Secure:
This is the most vital part of dealing with the private key, its security which is of utmost importance.
Are you aware that the strength of the private key depends on the key length and complexity? Yes, the lengthier the key, the more secure it is.
The next part is to keep the secret key in a secured location. This is done to prevent the key from falling into unauthorized hands.
The best way to secure the private key is to store the same on external hardware devices like Smart cards, HSM (hardware security modules), USB tokens, etc. This may help prevent intruders from accessing your data.
What Is the Role of Private Keys in Cybersecurity/SSL Certificates?
The private key carries the utmost importance in the cybersecurity world. It helps:
- Encrypt and/or Decrypt data
- Assert your Digital Identity
- Protect the Integrity of your Data
Encrypt and/or Decrypt data (ensures Data Privacy):
The private key secures the data and files exchanged between the client and the server and safeguards it from unauthorized personnel conducting MIM (man-in-middle) and other cyber-attacks.
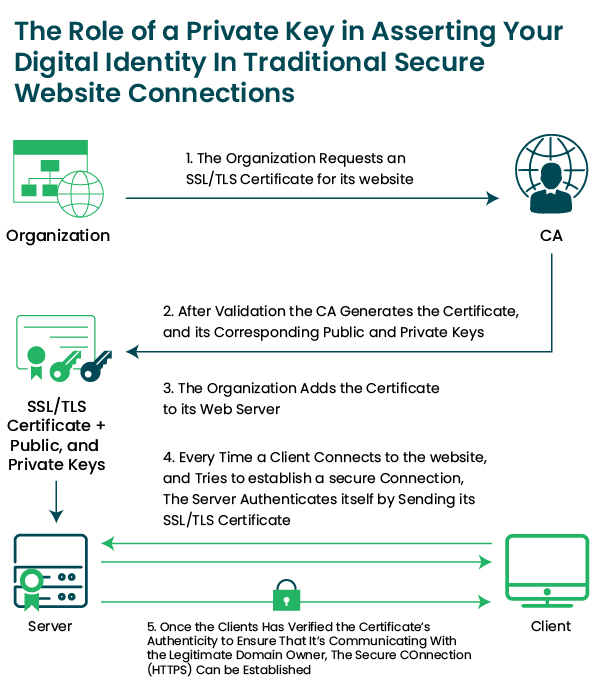
Assert your Digital Identity (portrays positive Identity Verification):
The private key helps portray a positive identity of your site and data. Since your digital identity is added and visible on your website and other digital connections like emails and social media accounts, users know that the website/connection they are approaching is legit and trustworthy.
Private keys are obtained from SSL/TLS certificates (Secure Socket Layer/Transport Layer Security certificates), which are issued by a CA (Certificate Authority) after proper verification. Hence indirectly, these private keys assure your positive and legit identity.
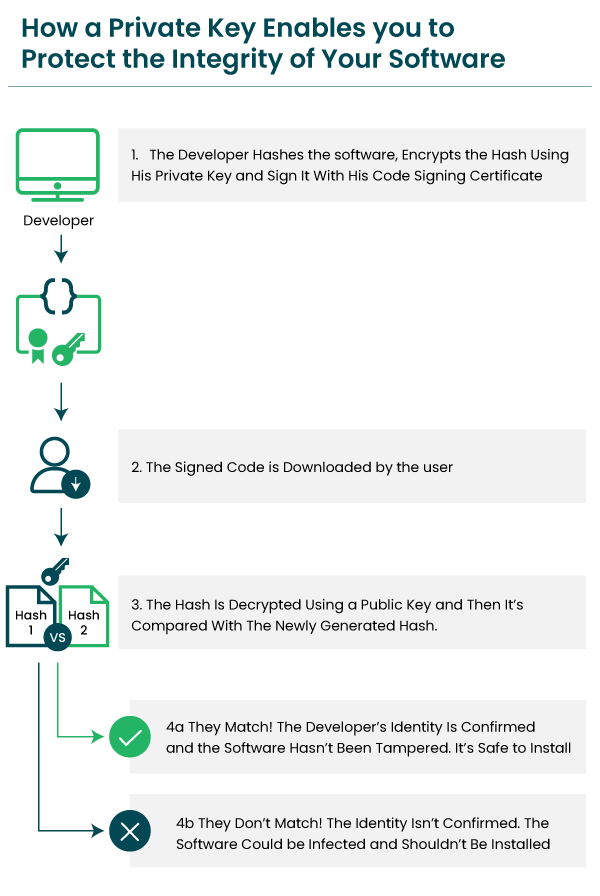
Protects the Integrity of your Data (using Cryptographic Algorithms):
Data integrity is maintained when the private keys and hashing algorithms combine to secure the site data.
Example: Code Signing certificates are a perfect example of ensuring data integrity. When these certificates are used for applying digital signatures on software, it ensures the customers that the software/app they are using or downloading is authentic and not tampered with.
How does a Private Key work?
Private key encryption, or symmetric encryption as you name it, uses only one key in the full encryption and decryption process.
Let us discuss the generation and the working of the private key in detail.
- Generating a New Private Key: A private key is created by the owner of the SSL certificate when they request the SSL certificate. The same is done by generating a Certificate Signing Request (CSR). Later, the site owner generates a private key by picking up a long random number.
- Securely Storing the Private Key: The most crucial factor of the private key is its storage. After the key is generated, it must be stored in a secured location. The keys can be stored on an external device or computer device, which is used to generate and encrypt/decrypt data.
It’s vital to secure these keys with a password encrypted or hashed for robust security. - Key Exchange: The private key, which is used in symmetric encryption, involves two processes, i.e., encryption and decryption. Since two parties (client and server) are involved, the key needs to be exchanged between these trusted parties to ensure data privacy. This process can be carried out by cryptographic software.
- Key Management: Public key pairs come with expiration dates; hence, key management is essential for securing data with the key pair. Data security and access to data are possible only when key management is appropriately handled.
The security of the private keys should be strong to prevent unwanted intrusions into your network.
Example: An expired public key certificate may compel browsers to display warning alerts stating that the site is unsecured.
In short, proper key management should be done to prevent the key pairs from being compromised or from facing expiration issues.
Conclusion for Private Key
Private keys can encrypt and decrypt data, whereas public keys can only encrypt the data. As digitalization grows, encryption security becomes more essential for secured browser-server exchanges.
Private key security is highly essential to ensuring communication and data security. The best way to secure them is to use external hardware like USB drives or hardware wallets. Your cyber security solution is incomplete without these keys, which are available when SSL digital certificates are installed on your server.
So, purchase SSL certificates from a reliable certificate provider and secure your digital presence.
Recommended Reading: