An Ultimate Encryption Guide: What is RSA & How does an RSA work?
Information exchange is the most significant aspect of modern businesses. Every company needs to provide data to users. Therefore, organizations ask to store, analyze and exchange user data.
According to The State of Email Security 2022, over 64% of companies have experienced ransomware attacks.
The rise in cyberattacks and higher possibilities of data leaks during information exchange needs reliable security measures. So, how will you ensure the security of data exchanged?
Cryptographic encryptions can help businesses secure their data. However, algorithms used for encryptions were not designed for secure data exchange without compromising the speed. For example, Diffie–Hellman (DH) algorithm used symmetric encryptions where two parties sharing data use a mutually agreed public security key.
However, it was effective encryption for non-sensitive data; crucial information needed a more reliable encryption protocol. This is where RSA changed the entire cybersecurity scenario through asymmetric encryptions. It has two separate keys for encryptions and decryptions.
Here, we will discuss RSA. How it works. The benefits of using it for your security systems.
Let us first discuss what is RSA!
What is RSA?
Rivest-Shamir-Adleman (RSA) is an encryption algorithm that uses asymmetric encryptions to secure data exchange between two parties.
There are two types of encryptions symmetric and asymmetric. Both of them differ in security key pair usage. Symmetric encryptions have the same key for encryption and decryptions, while asymmetric security keys are different.
Let’s take an example of a message you want to send to your friend to maintain secrecy. Now, if your friend lives on the other side of the world, the most logical way will be to send a message through email. However, email is not a completely secure channel.
However, if you can code sign the email, encryption will secure the message. Now, if you are using symmetric encryptions, you and your friend need to share the security key beforehand.
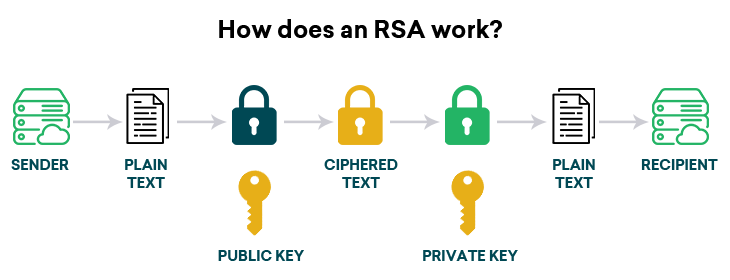
Such a scenario of mutually sharing the security key may not create a problem for you to secure the message. However, RSA solves a problem through two separate security key pairs. First, the message is encrypted using a public key and can be decrypted only through a private key.
RSA has several use cases, including digital signatures, SSL certificates, and the implementation of secure connections for VPN clients. It was a cryptographic algorithm first developed by Ron Rivest, Adi Shamir, and Leonard Adleman in 1977. The MIT-based academics created a one-way function for data exchange which was difficult for hackers to invert.
Key takeaways
- RSA encryptions are based on a mathematical approach called the trapdoor function
- It does not allow a function to be reversed without additional information
- The private key of the recipient provides that additional information allowing access to change function
- RSA enables the conversion of text, data, and images into anonymous information
- It provides encryption of emails, hard disks, online messengers, etc.
Now that we know what is RSA let us understand how it works.
How an RSA Works?
RSA is an asymmetric system where there are two security pairs generated. For example, public and private keys are two different keys generated for the encryption and decryption of data. However, a compelling use case of such encryptions is the usage of symmetric and asymmetric systems.
Many SSL certificate providers leverage RSA encryptions to encrypt symmetric keys. This provides a dual advantaFirst, symmetric encryptions have higher data transmission speeds, and an asymmetric system ensures better security.
But how does RSA ensure better security?
Now that we know how an RSA works, let’s understand the algorithm,
RSA Encryption Algorithm
Step 1 Key generation
It is essential to understand that security key generation needs complex mathematical calculations. So, if you want to generate security keys, the RSA algorithm will use the following approach,
- Two large prime numbers, X and Y, are chosen.
- These prime numbers need to be large enough for hackers to figure out.
- Calculate the totient function: F(n)=(X-1)(Y-1)
- Select an integer e which will act as a co-prime number to F(n) and 1
- Calculate d, which you can find through an extended euclidean algorithm
Here it is essential that (n,e) will be your public key and (n,d) will be your private key.
Step 2 Encrypting data.
Suppose the data is in a plaintext format known as P. Ciphertext that encrypts data P can be calculated as below,
C=Pe *modn
Step 3 Decrypting the data.
A data recipient needs a private key(n,d) to decrypt the data.
P=Cd *modn
RSA Algorithm Example
Here is an example of the RSA algorithm through pseudocode,
int x = 60, int y = 50;
int n = x * y;
// n = 3000.
// compute the totient, phi
int F = (x-1)*(y-1);
// F =2891
int e = findCoprime(F);
// find an 'e' which is > 1 and is a co-prime of F.
// e = 20 satisfies the current values.
// Using the extended euclidean algorithm, find 'd' which satisfies
// this equation:
d = (1 mod (F))/e;
// d = 2981 for the example values.
public_key = (e=20, n=3000);
private_key = (d=2981, n=3000);
// Given the plaintext P=123, the ciphertext C is :
C = (123^20) % 3000 = 820;
// To decrypt the cipher text C:
P = (820^2981) % 3000 = 123;
Advantages of RSA encryptions
RSA encryptions are the backbone of many security models creating a secure environment for organizations to exchange information.
- It provides more robust encryption than other algorithms
- The one-way function ensures irreversible data transmissions
- Two security keys help secure the message
- A secure channel of communication helps in preventing man-in-the-middle attacks.
- Cracking RSA encryptions require solving complex mathematical problems
- Implementing the RSA encryption is easy
- Transmitting confidential data with RSA is highly secure
Where is RSA encryption used?
RSA encrypts secure messages, protects websites from cyber attacks, and improves customer trust. For example, if you want to send a message securely, you must use mathematical calculations to create security keys. You need to know the recipient’s public key to encrypt data and provide a private key to decrypt it.
Similarly, if you want to code sign your applications to improve trust among customers and ensure that they can verify your identity, RSA can be helpful. You need first to hash the software and alert your recipient with a hash file to match it later. Further, code signs your app using the certificate provided by a certificate authority and append the hashed file.
Getting a code signing certificate using RSA encryptions or SSL certificates begins with generating a certificate signing request(CSR). Then, depending on the type of code signing certificate, you can provide details of an individual or organization to CA in CSR for the vetting process.
CA will verify details and issue a code signing certificate that uses RSA encryptions to secure data. Once you code the app, users can confirm their identity before downloading and installing the software.
You can also use RSA encryptions to,
- Implement RSA encryptions in systems like OpenSSL, WolfCrypt, Cryptlib, and other cryptographic repositories.
- Encrypt emails with RSA for higher security
- Establish a secure channel for TLS handshakes
- Secure VPN connections
RSA Vulnerabilities
RSA public keys result from two large prime numbers generated anonymously. So, the security of the algorithm depends on the prime factorization. In plain words, data security assumes that hackers can’t determine two random prime numbers within a specific time.
In theory, the assumption of two large prime numbers being secure does not always stand the test of time. In other words, in real-life scenarios, hackers can attack security keys through counter-algorithms like Greatest Common Deviser(GCD). So, there is no denying that public critical vulnerabilities are prevalent and can cause issues for RSA encryption.
Difference Between AES and RSA Algorithm
Comparison between AES and RSA algorithms is the debate of symmetric vs. asymmetric systems. Advanced Encryption Standard(AES) is based on encryption depending on the symmetric key. In other words, the same key is used for both encryption and decryption. Implementing the AES encryptions requires putting data and security keys in the software files.
Once AES is implemented, you will have encrypted, which is decrypted by putting the same key again in the software file. RSA provides a robust security system through two different security keys. So, you need a public key to encrypt and a private key to decrypt data.
Both have their advantages and disadvantages. For example, RSA is far more secure but slow. On the other hand, AES is fast but less secure. So, the best way to ensure higher security is to use both together.
You can use RSA algorithms to encrypt the security key of AES encryptions and ensure faster data transmission with enhanced protection.
Conclusion
Encryptions are one of the most effective security measures to ensure data protection. However, your systems will be vulnerable if you don’t choose a suitable cryptographic algorithm for your encryptions. RSA is one such algorithm that can help you improve security and protect user data.
Other algorithms like AES are popular, but the one-way function makes asymmetric systems efficient. Here we have discussed how an RSA works to protect your system, stands compared to AES, and its benefits. However, which encryption approach suits your system will depend on specific requirements.