Cybersecurity has seen many innovations over the years to counter the increasing risks of data theft. Ciphers have been a vital element of cybersecurity measures businesses use to protect their data. The SSL certificate is an example of how impactful ciphertexts have been to cybersecurity.
With SSL certifications, businesses have secured communications between multiple systems and improved user trust. This is why the SSL certificate market is growing at a CAGR of 18.4% and is expected to reach $9.6 billion by 2030.
So, there is no denying that businesses must invest in ciphers to ensure better data security. This article will help you understand cipher types and why you need them.
What is a Cipher?
A cipher is a cryptographic algorithm that you can use for encrypting and decrypting the data. It is a process of scrambling the data into an unreadable format that the receiver can access through decryption. Decrypting a message begins by solving the mathematical equation on a cryptographic algorithm and converting the scrambled information into readable format.
How Does a Cipher Work?
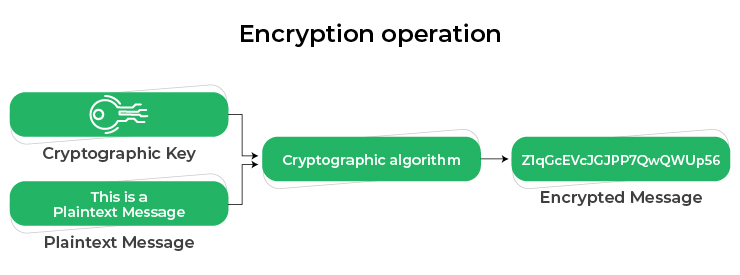
Ciphers use a system of fixed rules and an encryption algorithm. It can transform any message or data into a ciphertext using the algorithms. It is a string of random characters that help you ensure the information is hidden from cyberattackers.
You can use these ciphers to encrypt and decrypt data in streams known as stream ciphers. Another way to use it is by processing the ciphertext in uniform blocks of specific data bits, also known as block ciphers.
Cipher implementations depend on algorithms and a secret security key. Encryption algorithms use the secret key to convert data into a string of random characters, which is only convertible back to plain text through another key.
A key aspect that you need to keep in mind while using ciphers is the key length. Data protection is better if your secret key size is higher, especially against brute-force attacks. A secret key of at least 128 bits is the most secure against brute force attacks.
Importance of Secret Key for Ciphers
A secret key is crucial for any encryption algorithm because encryption and decryption are impossible without it. Even if the algorithm is made public, the security key is hidden because cyberattackers can leverage it to attack the systems.
Encryption algorithms use two different types of keys
- The public key, which is shared with everyone
- Private or the secret key
The type of encryption depends on how you use the security keys. For example, using the same key for encryption and decryption is called symmetric encryption. On the contrary, using one key for encryption and another for decryption is called asymmetric encryption.
Cipher Use Cases You Need to Know
Symmetric ciphers or algorithms provide security through the same encryption and decryption keys, which makes them ideal for securing online communications. You can integrate them into your network protocols and secure the data exchanges. A simple example of using symmetric ciphers is data encryptions through Secure Sockets Layer or TLS certificates.
Another important use case for symmetric ciphers is securing the remote data connections. For example, Virtual Private Networks or VPNs connect with remote branches of the network using symmetric ciphers. This helps in securing the network communications between systems through HTTPS protocols.
Importance of Ciphers in Cryptography
Cryptography helps businesses achieve better information security and protect enterprise data from key cyber threats. It secures transactions, communications, and personally identifiable information(PII). If your cryptographic algorithm is weak, it can lead to data leaks. This is why your algorithm needs a reliable cipher to ensure higher security for your data.
Some of the key benefits the cipher offers to cryptographic algorithms are,
Confidentiality protection
Businesses need to secure sensitive information and transactions across applications. Not secured can lead to data leakages and compliance issues for your organization. Ciphers offer protection for your sensitive data through encryption algorithms.
Data integrity
Managing users ‘ financial data becomes crucial whether you are an eCommerce business or a fintech startup. PCI DSS is a standard that most eCommerce organizations and banking institutions must comply with.
This is where ciphers can help businesses with data integrity. Another important aspect of using a ciphertext is the integrity of applications. Cipher-based SSL certificates can help users verify the authenticity of an application and ensure its data integrity is intact.
For better data integrity and strong validation, EV SSL certificate is an essential security for business platforms.
Authentications for data access
Data access authentications require verification of the person assigned specific permissions. This is where ciphers can help you authenticate a person with access permissions. It also allows you to authenticate root access to website admin.
Now that you know the benefits of using ciphers, it’s time to know which type you can choose for your business.
Different Types of Ciphers in Cryptography
There are many different types of ciphers that you can use for your data security. For example, if you want to encrypt specific data, you can use substitution ciphers. Similarly, you can leverage transposition ciphers to scramble the alphabet formation of a word and make it unreadable.
Substitution ciphers:
In this cipher type, you can replace the bits and characters in plaintext with alternate bits. Substitution ciphers are two types:
- Monoalphabetic – You can encrypt a single alphabet from the plaintext message.
- Polyalphabetic – You can encrypt mixed alphabets to secure each bit or character with a more complex algorithm.
Transposition ciphers:
Rather than changing the alphabet with alternate bits, transposition ciphers allow you to rearrange each character in the plaintext message. Take an example of a simple columnar transposition ciphertext where you can read the message horizontally but in a vertical arrangement.
Polygraphic ciphers:
With this cipher type, you can substitute a group of alphabets in the plaintext message. You can use this cipher to substitute two or more groups of alphabets by masking frequency distribution for letters.
Private key cryptography
From different types of ciphers that you can use, this is the one where a shared key is used. Both sender and receiver have a security key pre-shared. The same key encrypts and decrypts the data. This is why it is also known as symmetric encryption.
Public key cryptography
This is the opposite of private key cryptography. There are two sets of security key pairs, public and private. Separate keys are used for encryptions and decryptions. This type of cipher is also known as the asymmetric encryption.
Key takeaways
Increasing cyberattacks and the need for better security require robust encryptions. This is why it is important for you to understand what ciphers are, their importance for data encryption, and their different types. However, which type of cipher to use for your data encryption will depend on the specific security requirements of your system. .
Related Post: