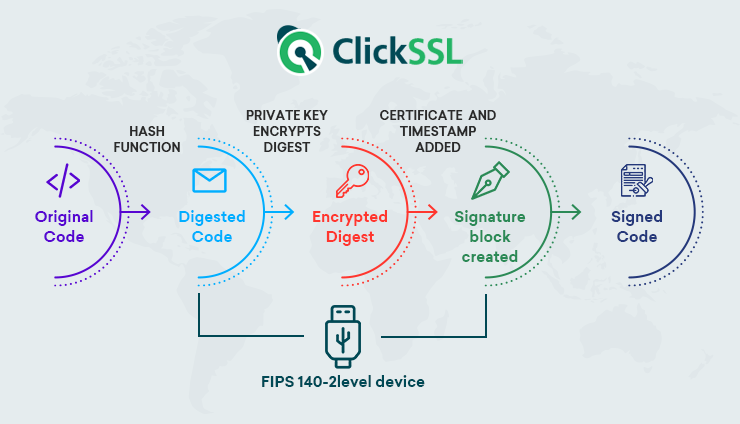
A Code Signing Certificate is a digital certificate used by software developers to sign the code of their software and app. It uses the public-private key infrastructure (PKI) to bind the entity to the public key and a private key.
What is Code Signing Certificate?
Code Signing Certificate is a digital certificate which confirms that the software comes from a trusted source and is not altered or tampered with.
It authenticates the code integrity and publisher’s identity so that the users can safely download any software or applications.
Code signing certificates are commonly used by software developers and publishers to distribute their applications securely.
Most Operating Systems (OS) come preloaded with the digital signatures of leading Certificate Authorities (CA) and thus determine an application’s compatibility level based on that.
How Does Code Signing Certificate Work?
Code Sign Certificate follows a certain process that we can understand from the below points.
#1. Purchase Code Signing Certificate
First, you need to buy code signing certificate, and the certificate follows the organization and extended validation process. An individual or a company can apply for a Code Signing certificate.
#2. Verify Identity
Once you apply for the certificate, the certificate authority (the CA) undergoes the verification process depending upon the type, like an individual or a company. The certificate authorizes the identity to ensure users that they are downloading software from the original source.
#3. Certificate Installation
After getting Code Signing certificates, you need to install them on the desired platform. When you start signing executables and scripts, the process of signing on each platform seems different.
The code is signed with a digital signature, and a string of data being hashed that shows the publisher’s identity also ensures that the code is not changed since it is signed. A digital signature shows your identity information when you signed a software, driver, or application.
#4. Distribute Software
After signing the software, it is time to distribute it. Users will see a signature while downloading software. The software will show your verified publisher’s identity during downloading. It also assures that the code remained intact since it is signed.
It is wise to timestamp your code as it will keep the code valid even if the certificate is expired. Each certificate comes with a validity period. Users will have no unwanted warning when they download the software.
Types of Code Signing Certificate
Code certificates can be classified into two types based on the level of validation sought — Organization Validation (OV) Code Signing and Extended Validation (EV) Code Signing.
The core difference between the two is the CA’s verification level and how the private key is stored. Both these types make use of public-private key cryptography and allow the applicant to encrypt the code.
OV Code Signing Certificate
An OV code signing certificate can be obtained much faster because, in this case, the CA performs primary verification only. This includes verifying details such as the developer’s identity, the organization’s name, phone number, and the applicant’s physical address.
Once approved, the private key is issued to the applicant, who can store it on his system just like the private key of an SSL certificate is stored. However, this may not always be secure and must, therefore, be avoided unless you are looking for a price benefit.
EV Code Signing Certificate
EV Code Signing Certificate is an advanced code signing cert and is ideal for serious publishers who are ready to undergo a comprehensive vetting process. This is carried out following the guidelines laid down by the CA/Browser Forum. The documentation required for its approval usually includes everything mentioned for the OV Certificate.
In addition to that, the applicant would be required to furnish a business registration certificate, an attestation from a government organization or a Chartered Public Accountant, and a business profile created by a reputable information source. Once the EV code signing certificate is issued, the applicant would be required to store the private key in an external hardware token, making it a safer option for software development firms and companies.
OV vs EV Code Signing Certificate — Which One Should You Choose?
If you are confused between the EV and OV code signing certificates, we recommend choosing the EV code signing certificate as it comes with advanced security features. The CA sends an encrypted USB which is essential for the code signing, and this sort of two-factor authentication eliminates the possibility of unauthorized access.
Also, the Microsoft SmartScreen recognition, which comes with the EV code signing certificate, lets you build more trust. If the price is a concern, you may stick to the OV certificate, a pocket-friendly alternative. However, if you are signing Windows 10 drivers, you should invest in an EV code signing.
Recommneded: EV Code Signing Certificate vs Standard Code Signing Certificate
Benefits of Code Signing Certificate
In the internet landscape, there is little or no communication between the application developer and the end user. Cybercriminals often misuse this gap for their personal gain. Thus, CAs bridge this gap digitally by verifying the publisher’s credentials and binding their identity to the code or the script. This brings along many benefits for the developer and the end-user and makes the internet safer.
Let us now discuss some of the core benefits of using a signing certificate to make your code signed with strong encryption.
#1. Timestamping
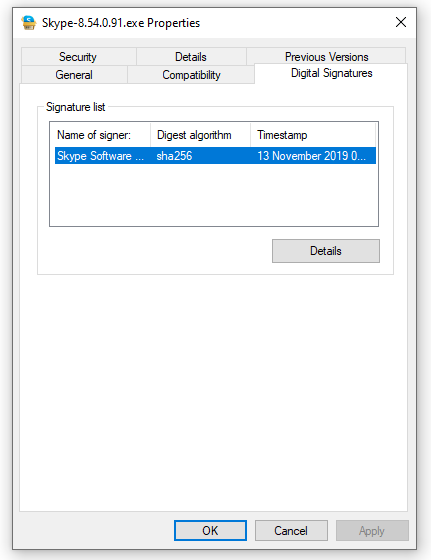
Whenever the developer applies the digital signature, a timestamp is also applied, and the hash of the code is sent to the server. The best part is that this timestamp remains valid indefinitely even after the certificate expires. Users can check a timestamp easily by right-clicking the executable file and navigating to properties. There, the timestamping details can be found under the “Digital Signature” tab. It can be accessed by clicking on the ‘Details’ option.
#2. Enhanced Security
Over 24,000 malicious applications are blocked every day, explaining why the average user hesitates to trust any internet application. Users are always worried about their personal and financial data being stolen by prying cybercriminals. This gets worse when they see a security warning being flashed by their operating systems. One way to tell your users that the application is safe and untampered with is by encrypting its code with the code signing certificates. It protects the integrity of the code, improves security, and communicates the same to the end user.
#3. Code Authentication
Threat actors are all over the internet injecting malware into applications to steal credentials, gain unauthorized control over the installer’s system, or for other illegitimate purposes. Developers can prevent this through the hash function, which warns the user in case of any tampering with the code.
#4. Builds Trust
This digital certificate builds more trust between the vendor and the app user because it comes with a third-party seal. Moreover, the user can check the timestamp, which is affixed to the code when the digital signature is used. Finally, the fact that the certificate eliminates security warnings and installation errors adds to the trust factor.
Code Signing Certificates Best Practice
To ensure the code’s safety, you need to follow a few best practices to keep the Code Signing cert effective.
#1. Control Access:
There should be limited access to a private key as a human factor is responsible for handling a private key. Role-based access can limit the chances of exposure to a private key. If a hacker accesses a private key, there are chances of the distribution of malicious code to users.
#2. Test Signing Certificate:
A publisher should use a self-sign certificate or the certificate issued by a private certificate authority for a code’s prerelease. The testing should be done in a secure environment. It may be the case where the same level of encryption and chain to the same root certificate is not presented in a self-signed certificate.
#3. Increase Key Standards:
A publisher should use a hardware security module or security vault to keep a private key safe from prying eyes. The key protection product should pass FIPS-140 Level 2 certification. Hardware should have a strong password that includes lowercase, uppercase, numerical, and special characters.
#4. Malware Scan:
Before signing a code, a publisher should run a scan as Code Signing only sings the code but does not look inside it. It is necessary to execute virus and malware scanning for a code. When you use open-source code from an external source, you should be very careful. Any change in a code should be manually verified.
#5. Expired Certificate:
If any certificate is compromised, immediately revoke it. A compromised certificate may indicate that the hacker has access to the private key. There are chances that the certificate used for application signing may contain malware.
What if My Code Signing Certificate Expires?
If the signing certificate expires, you will have to renew it or buy a new one and install it to protect your software application. Even when the certificate expires, the timestamp continues to be there indefinitely. A good practice would be to provide the CA with an email ID that you regularly use to receive alerts before the expiry of the code signing certificate.
Final Takeaway for Code Signing Certificate
The code signing certificate allows developers to securely share their applications over the internet without the fear of the script or code being tampered with. Also, it confirms that the code or the script comes from the source mentioned in the certificate and that the CA has verified the same. This prevents miscreants from inserting malicious code and compromising the security of the end user. However, to create a truly secure application, the developer must opt for an EV Code signing which significantly reduces unauthorized access.
Recommended Reading: