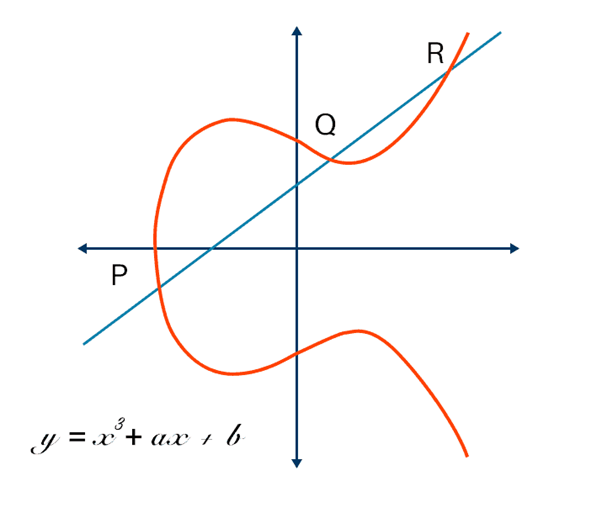Understand the difference between ECC and RSA certificates. Secure your data against cyber threats with ECC and RSA certificates.
In January 2023, T-Mobile discovered a significant data breach through APIs affecting over 37 million customers. Such cyberattacks are becoming more common among businesses. However, if you are a business dealing with security issues, a simple way to reduce the risk of data breaches is by installing digital certificates.
Digital certificates use encryption algorithms to secure the data from being exposed. When you think of encryption algorithms, ECC vs RSA is an essential discussion. It allows you to understand which technology you need to secure data. This article will help you know the difference between ECC and RSA algorithms to improve the security of your systems.
What is RSA?
RSA(Rivest-Shamir-Adleman) is used extensively to enable cryptosystems or a suite of algorithms. RSA algorithms would allow businesses to deploy public key encryptions. It secures the data sent in an insecure network like the internet.
In public key cryptography, there are two types of algorithms. One is a symmetric algorithm with the same security keys used for encryption and decryption. On the contrary, the second type of encryption algorithm, the asymmetric algorithm, ensures that security keys for encryption and decryption are different.
RSA is an asymmetric algorithm where a public key can encrypt the data, and private keys can be used to decrypt. Similarly, a private key can be used for encryption, and a public key can be used for decryption.
So how does it work?
RSA uses mathematical trapdoor functions and number theory to deploy encryption. Data encryption in RSA algorithms begins by creating a modulus n =pq. P and q are two prime numbers multiplied to generate a modulus.
Further, a public exponent “e” is selected, which is the product of two elements (p-1) and (q-1). Next, a private key is generated using the modulus n and d, where d is the mod of (p-1)(q-1)=1.
To encrypt data, you need to raise the power of “emodn” and to decrypt the information, the receiver needs to deploy ciphertext to the power of “dmodn.”
While this process uses prime numbers and mathematical equations to secure data, RSA’s robustness makes it an attractive choice. Breaking such a pattern with high-level mathematical equations takes a lot of work.
Features of RSA
- RSA uses security key pairs, which are different for encryption and decryption. This asymmetric encryption process ensures better security between two systems exchanging data,
- RSA key sizes like 512, 1024, 2048, and 3072 bit provide many security options for businesses. It is important to note that the higher the critical size number, the better the security.
- Breaking two large prime number modus to decrypt the data is difficult for any cyber attacker, making it one of the most secure algorithms.
- You can also use RSA for digital signatures, helping to prove the authenticity of your web apps.
What is ECC?
Elliptical curve cryptography(ECC) is another asymmetric algorithm that secures the communication between two systems. ECC uses an elliptic curve’s algebraic over infinite fields at its core to facilitate encryptions.
ECC uses an elliptic curve discrete logarithm problem (ECDLP), which is not easy to break for cyber attackers. Breaking ECC requires solving a mathematical equation, which is not easy. This equation results in an elliptical curve in the graph, so hackers need to use brute-force attacks to break ECC.
If you use the mathematical equation of y²=x³ + ax + b to plot an elliptic curve on the graph, it will define the cryptographic encryption that ECC employs. The process begins by choosing the graph’s private and public key points. Here, a and b are coefficients of the curve, with X and Y being coordinates.
The points need to be plotted to satisfy the elliptic curve equation. During the encryption process, a point on the curve is the public key, and the second is the private key. A series of mathematical calculations are completed to complete the encryption process, and ciphertext is created.
Next, the same mathematical equations must be executed on the ciphertext and private key to decrypt the data. Its key length makes it worthy of consideration in the ECC vs RSA debate. It provides the same security level as RSA but has a shorter key size.
Features of ECC
- ECC has a smaller key size, making it more attractive for businesses with database constraints.
- ECC offers the same protection that RSA can offer but with the benefits of lightweight encryption keys
- Due to smaller key size the load handling capacity of systems is optimized making it ideal for businesses.
- The faster and lightweight computational capabilities of ECC make it the best cryptographic algorithm to choose for encryptions.
RSA vs. ECC: Comparing Algorithm Strength
The performance of RSA and ECC algorithms can be measured by analyzing the key generation and processing time. According to a performance review on 163-bit ECC/1024-bit RSA security level, an elliptic curve is generated for general curves over the field approximately 5-15 times faster than RSA private key generation.
| Key Length | Time(s) | ||
|---|---|---|---|
| RSA | ECC | RSA | ECC |
| 1024 | 163 | 0.16 | 0.08 |
| 2240 | 233 | 7.47 | 0.18 |
| 3072 | 283 | 9.80 | 0.27 |
| 7680 | 409 | 133.90 | 0.64 |
| 15360 | 571 | 679.06 | 1.44 |
Comparing the performance at 256-bit ECC/3072-bit RSA security level, the ratio of fields increases to 20-60. The performance comparison of ECC vs RSA indicates that ECC key generation outperforms RSA. Since ECC does not require more resources due to its shorter key length, it has an edge over RSA.
Which Certificate Authorities offer ECC Certificates?
A certificate authority is a trustworthy entity that issues a certificate after verifying the requestor’s details. Once you compare ECC vs RSA and decide to use ECC algorithm certificates, selecting the right certificate authority is important.
Some of the significant CAs that provide ECC certificates are,
- DigiCert
- GlobalSign
- Comodo SSL
- Sectigo
- Certicom.
These CAs provide ECC certificates with different features; you can compare them to decide the most suitable one.
Key takeaways of ECC vs RSA Certificate
Both ECC and RSA algorithms help you secure data from many cyberattacks. However, comparing ECC vs RSA is crucial to deciding which certificates to use to secure your websites. Once you compare, there will be clarity on choosing ECC certificates over RSA due to shorter key sizes, lightweight processing, and higher security.
Related Post: